Content

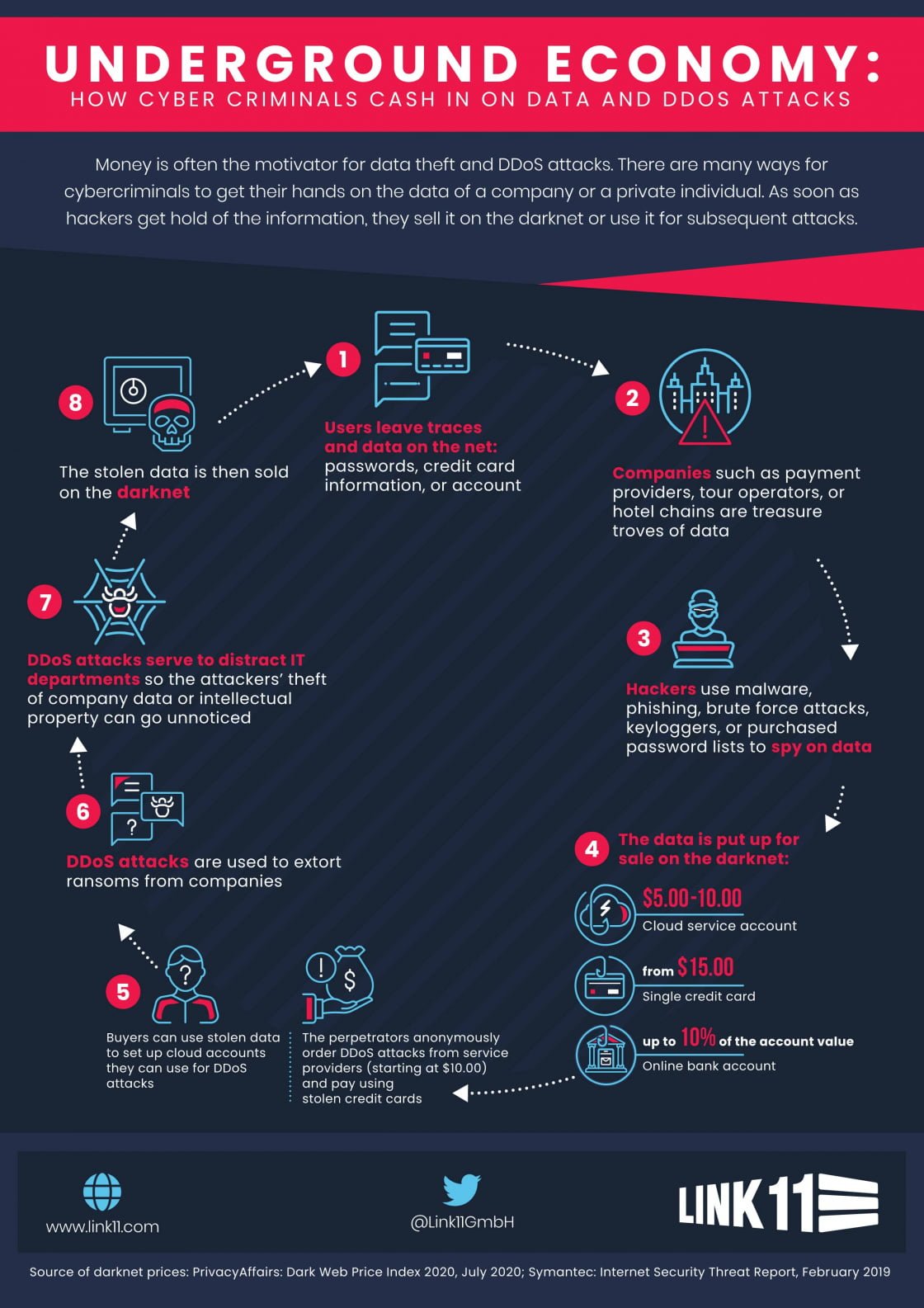
Like the real digital economy, an underground economy has developed that also has differentiated value chains. In many cases, these are based on data, whose increasing commercial value makes them attractive to cybercriminals. Value creation comprises several stages and can be roughly divided into the following phases:
- Spying on data
- Selling data on digital marketplaces or blackmailing companies
- Using purchased stolen data for more cyber-attacks.
Spying on data
Besides end users (i.e., consumers), it is mainly organizations that generate data. By 2025, companies are expected to be responsible for 80% of the total amount of data, which will include usage data, production data, customer databases, and data about the companies themselves. Tour operators, banks, insurers, and online retailers are sitting on huge data treasures. Just how large these data stores are becomes painfully clear whenever there’s a data theft or a data breach. The criminals use various methods to gain access to a company’s networks and databases. They exploit outdated software or inadequately configured firewalls (malware) or hijack mobile devices or weak passwords (brute force attacks).
Data is sold
You can buy and sell anything on the Internet – including illegally obtained private data. Cybercriminals who possess stolen data usually don’t risk misusing the data themselves. It’s much safer and more profitable to resell it. Digital marketplaces have become the ideal trading ground for data. Buyers and sellers meet on both the darknet and on the clear web. Depending on the quality, scope, and timeliness of the data, prices range from a few U.S. cents to one U.S. dollar per data record. The fact that data can be sold multiple times increases the cybercriminal’s profit. Payment is usually made with anonymous cryptocurrencies such as Bitcoin. A newer variant relies on blackmailing a company with the stolen data. If the victims don’t pay, the data ends up on the Internet.
Purchased data enables cybercrime infrastructure to expand
Using the purchased data, cybercriminals can execute various activities on the Internet, such as shopping online or using digital payment services. These forms of identity theft are all about making a quick buck and getting rich. Another use of the data is to create accounts on public cloud services. The perpetrators rent cloud-computing power that’s billed to the credit card data they purchased. They use pre-written scripts to automatically check which data is valid for an account login. Furthermore, the perpetrators gain access to existing cloud accounts via insufficiently protected APIs and manipulate them. The subsequent implantation of malware on the virtual servers, which helps them launch various cyber-attacks, is child’s play for the criminals. Especially in DDoS attacks, which attacker’s use to systematically overload a company’s servers and networks, the fake cloud accounts have proven their worth. The reason: cloud computing offers an unlimited amount of computing power and high-bandwidth Internet connections. They are ideal vehicles for powerful attacks.
Cyber extortion generates money
DDoS attacks pose huge dangers for because, for a company whose IT is not adequately protected, they can lead to prolonged downtime for important services and entire systems. So-called DDoS extortionists are attacking companies more and more frequently. With the help of rented cloud servers, they attack their victim’s IT infrastructure and send them ransom demands by e-mail. In many cases, the sums involved are in the six-figure range. If the company does not pay, it is attacked again. Only if the cybercriminals detect effective DDoS protection installed in the IT infrastructure of their victim do they refrain from the extortion.
Sometimes the operational rush to defend against an ongoing DDoS attack is precisely calculated by the attackers. They design the attacks as a diversion that keeps the enterprise IT team busy. Meanwhile, the criminals gain unnoticed access to the company network in the background and infiltrate malware or steal data. It often takes weeks or months before a data theft is noticed and linked to previous attacks.
It is therefore crucial for companies to correlate these activities and check whether there have been any other anomalies. The data volumes that need to be monitored for complex anomalies are almost unmanageable for humans. For artificial intelligence this task is easy. It correlates the data in real time and thus helps companies avoid IT security silos.