Content

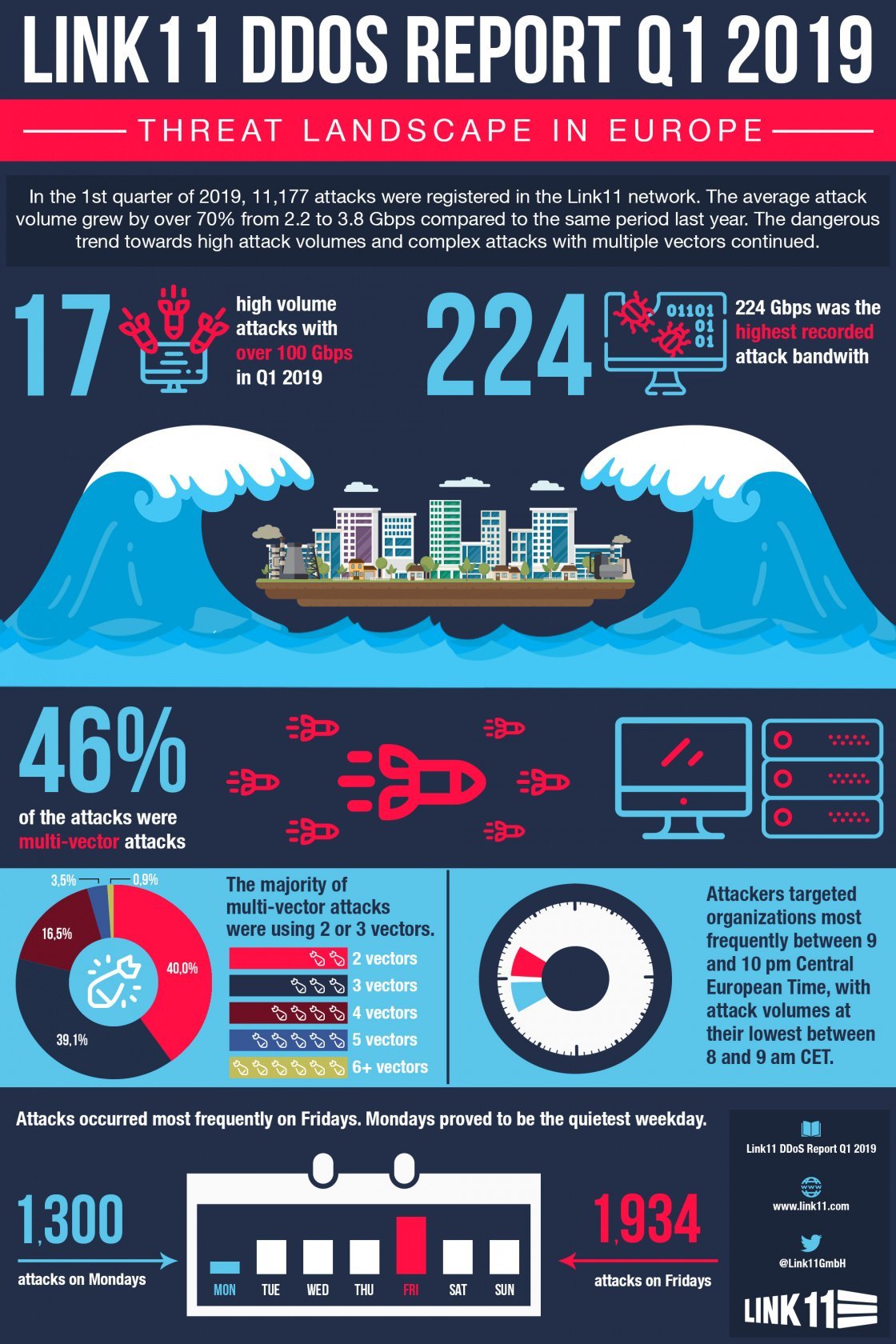
Europe continues to be a target for DDoS attacks, as the current DDoS attack figures from the Link11 Security Operation Center show. Link11 registered 11,177 DDoS attacks on targets in Europe in Q1 2019. These high attack volumes and the large number of different attack vectors pose significant challenges to companies that lack appropriate protection.
DDoS attacks achieved volumes of over 100 Gbps a total of 17 times during Q1. The peak DDoS attack bandwidth was 224 Gbps. In addition to the 17 attacks of 100+ Gbps there were another 8 attacks in the range 80 to 100 Gbps. The mean bandwidth was 3.8 Gbps. This represents an increase of more than 70% compared with the 2.2 Gbps recorded during the same period of the previous year.
DDoS vectors overload Internet connections and system resources
In order to increase the effectiveness of their attacks, attackers relied on insufficiently-protected Internet services such as DNS and NTP. DNS was the reflection amplification vector used in most attacks in the 1st quarter of 2019. The second most used was the Connectionless Lightweight Directory Access Protocol (CLDAP), which the perpetrators used to increase bandwidths.
One year after the memcached reflection attack vector emerged, this vector has almost disappeared again. According to analyses conducted by LSOC, the vector, which set new bandwidth records in the Terabit range in late February/early March, has only been used in 160 attacks since and played no role in attacks above 80 Gbps.
DDoS attacks with the HTTPS vector, on the other hand, were less aimed at high bandwidths (for example UDP reflection amplification attacks), than they were at disguised legitimate user requests. Instead of overloading the connection, they exploit server resources by decrypting and encrypting SSL connections. HTTPS attacks are barely visible and difficult to detect because it is quite difficult to distinguish the manipulated traffic from normal requests without inspecting the packets. Only granular insight into the via TLS/SSL-encrypted traffic can reveal such attacks.
Multi-vector attacks combine up to 8 techniques
46% of attacks were multi-vector attacks with multiple attack techniques targeting different vulnerabilities at the volume, protocol, and application levels. The perpetrators either use them simultaneously or start them at different times. Complex attacks with 2 or 3 vectors represented up to almost 80% of multi-vector attacks.
Distribution according to the number of attacks used.
| Number of vectors | Share |
| 2 vectors: | 40,0 % |
| 3 vectors: | 39,1 % |
| 4 vectors: | 16,5 % |
| 5 vectors: | 3,5 % |
| 6 vectors: | 0,8 % |
Attack detection using artificial intelligence and machine learning
The secure detection and defense of multi-vector attacks in DDoS protection is based on the use of artificial intelligence (AI) and machine learning (ML). The algorithms used to detect the various vectors differ from one another and must be combined to reliably detect attacks. AI and ML are used to compare thousands of data points from the packet inspections continuously and in real time. This enables them to detect connections and underlying attack patterns and automatically start filtering data traffic.
DDoS attacks depend on the month, day and time
The distribution of DDoS attacks was uneven in the first quarter of 2019. In January, LSOC registered the most attacks at 4,422, followed by March with 4,037 and February with 2,718. The daily maximum of attacks in the 1st quarter 2019 was 314 attacks (03/15/2019).
The DDoS threat also depended on the day of the week, and the time of day. The largest number of attacks took place on Fridays (17%). The lowest share, just under 12%, was registered on Mondays. The highest number of attacks began between 9pm and 10pm; the lowest number of attacks began between 8am and 9am.
It is interesting to note that the attacks in March lasted much longer with an average of 13 minutes compared with the attacks in January which averaged almost 8 minutes. The longest attack lasted 718 minutes.
Marc Wilczek, Link11 Managing Director: “The current figures regarding attack volume, reflection amplification and complex attack patterns show how important it is to secure business processes and digital structures against DDoS attacks. The perpetrators target all levels of corporate IT. This makes it all the more important to proactively identify potential DDoS vulnerabilities. Signature-based attack detection is no longer sufficient in view of dynamic threat situations. The proactive use of artificial intelligence and machine learning, which recognize the differentiated behavior strategies of attackers, is a must.”