Content
IP fragmentation attacks – how do they work?
To understand IP fragmentation attacks, it is important to understand IP fragmentation first. IP communication is used to exchange data packets on the internet. Between their source and their target, the packets often have to be passed along by various connection technologies and systems.
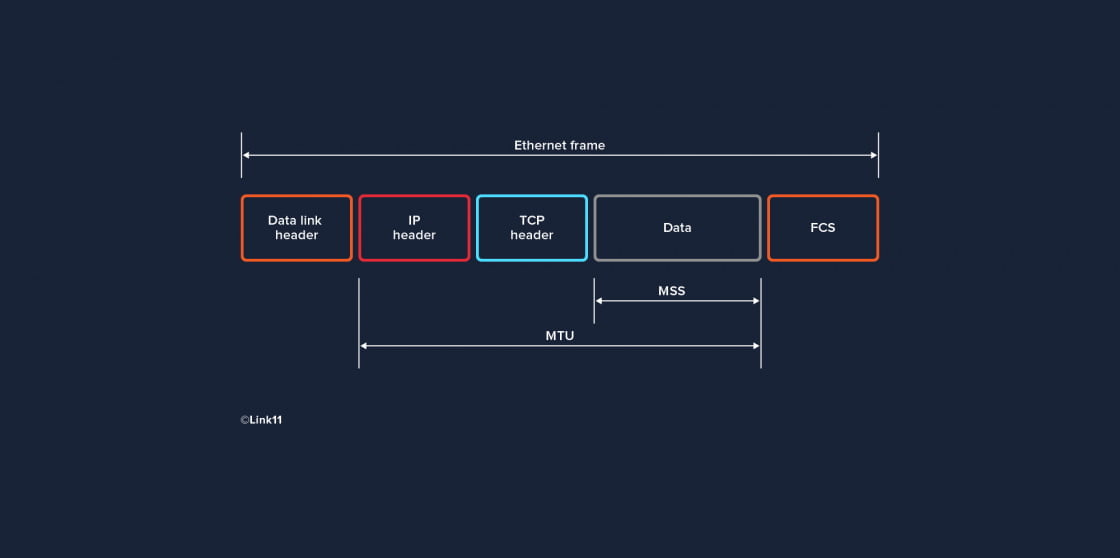
The great number of technologies involved leads to limitations that make it necessary to fragment IP packets. This is because different data transfer systems have different MTUs (maximum transfer units).
The MTU indicates the maximum IP packet length or size for a given network type or data transfer system. The network sets an upper limit for the MTU, but it may be smaller. The smaller it is, the more the data payload is fragmented during transfer.
In this context, another term related to MTU is often mentioned: MSS (maximum segment size). The concepts are related but should not be confused. MTU is the maximum volume of the entire data packet, while MSS indicates the volume of the data payload within the packet.
Different MTU sizes of various network types in bytes
| Network type | MTU |
|---|---|
| Ethernet | 1500 |
| Token ring, 4 Mbps | 4464 |
| Token ring, 16 Mbps | 17914 |
| IEEE 802.3 | 1492 |
| X.25 | 576 |
| FDDI | 4352 |
IP fragmentation divides the packets or datagrams in such a way that they can be transmitted by a certain network type. The task of reassembling them is left to the target. The following IP header fields are important for this:
- Source IP
- Destination IP
- Identification
- Total length
- Fragment offset
- Flags
Example of a fragmented IP datagram
| Sequence | Identifier | Total lenght | DF may/don’t | MF last/more | Fragment offset |
|---|---|---|---|---|---|
| 0 | 567 | 5180 | 0 | 0 | 0 |
Original datagram
IP fragments
| Sequence | Identifier | Total lenght | DF may/don’t | MF last/more | Fragment offset |
|---|---|---|---|---|---|
| 0:0 | 567 | 1500 | 0 | 1 | 0 |
| 0:1 | 567 | 1500 | 0 | 1 | 185 |
| 0:2 | 567 | 1500 | 0 | 1 | 370 |
| 0:3 | 567 | 740 | 0 | 0 | 555 |
How can this be used for attacks?
IP fragmentation can be abused in various ways by attackers. It can be employed to attack the IP communication’s target system but also security components along the way towards the target system.
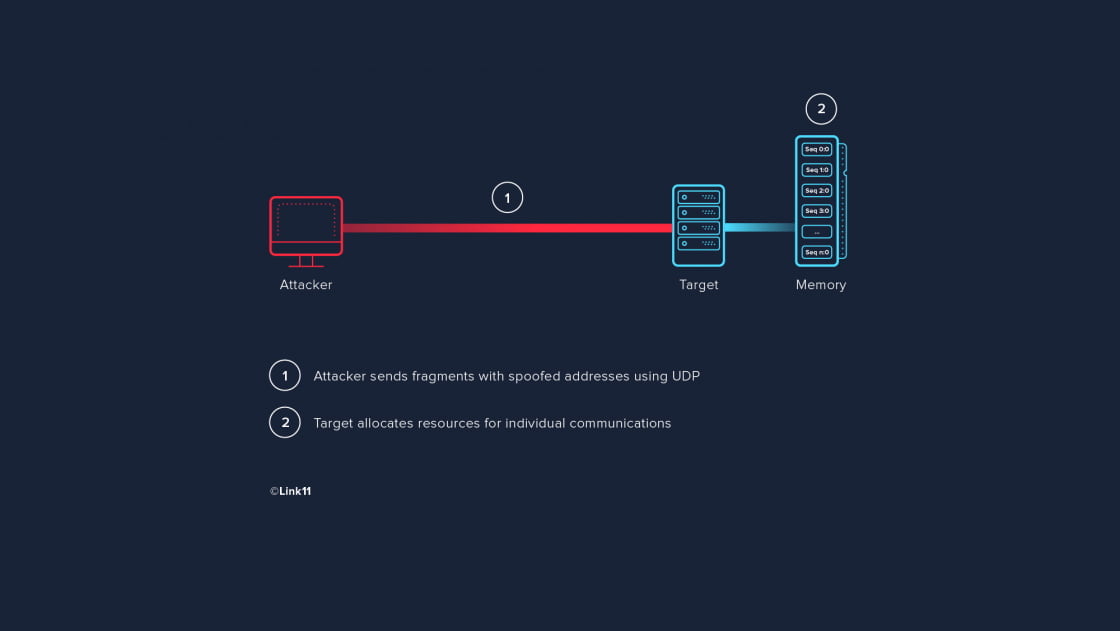
Reassembly (defragmentation) can only take place when all fragments are in. UDP/ICMP-based fragmentation attacks usually submit fake fragments that cannot be defragmented. Temporary storage of the fragments takes up memory and, in the worst-case scenario, may exhaust the available memory resources. An attack like this may use packets of the following type:
| Sequence | Identifier | Total length | DF may/don’t | MF last/more | Fragment offset |
| 0:0 | 100 | 1500 | 0 | 1 | 0 |
| 1:0 | 200 | 1500 | 0 | 1 | 0 |
| 2:0 | 300 | 1500 | 0 | 1 | 0 |
| 3:0 | 400 | 1500 | 0 | 1 | 0 |
| 4:0 | 500 | 1500 | 0 | 1 | 0 |
| … | |||||
| n:0 | x | 1500 | 0 | 1 | 0 |
Each fragment is the first fragment of a datagram and announces more fragments. As a result, the processing hosts and layer-7 security components reserve resources for all “n” communcations:
A TCP-based fragmentation attack (also known as teardrop), however, is usually directed against the defragmentation mechanisms of the target systems or security components. Overlapping packets are sent that, in extreme cases, may lead to the target system freezing up, depending on the operating system.