Content
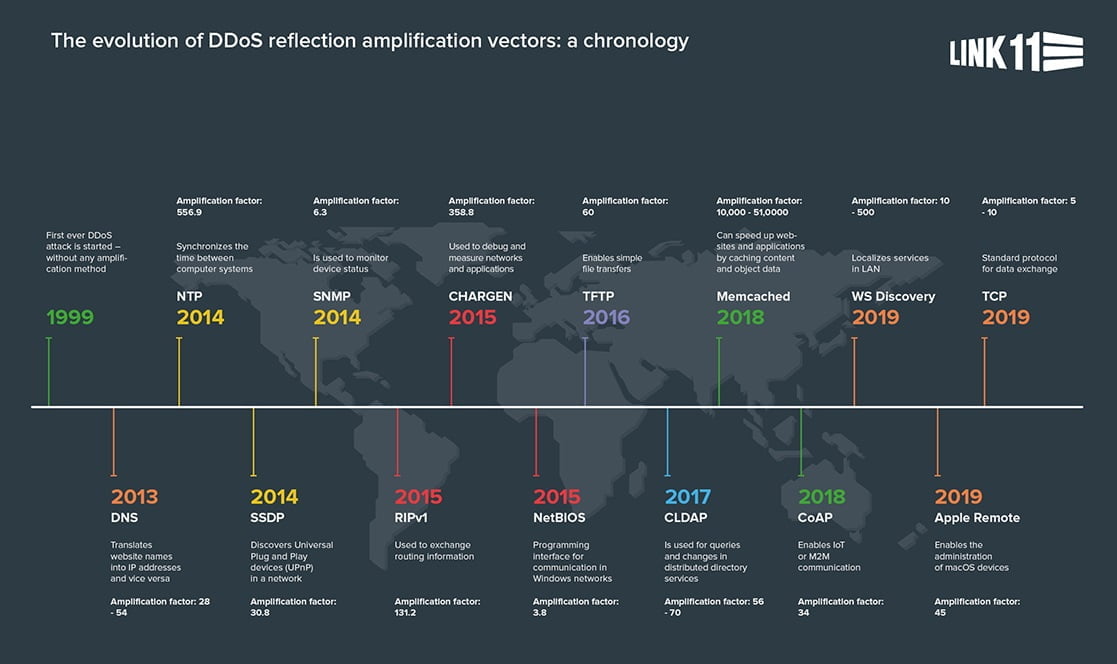
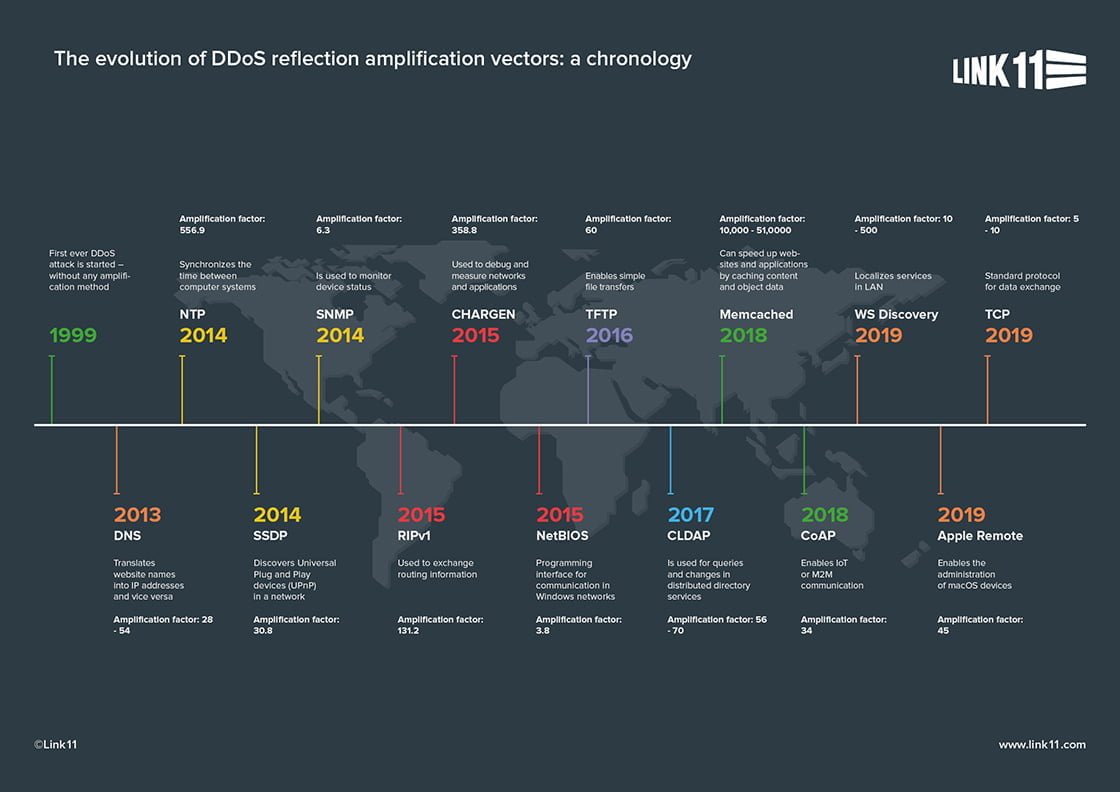
The first reflection amplification vectors occurred in 2013 and involved DNS and NTP. Since then, the spectrum of vectors has become far greater. Currently, there are over 20 techniques.
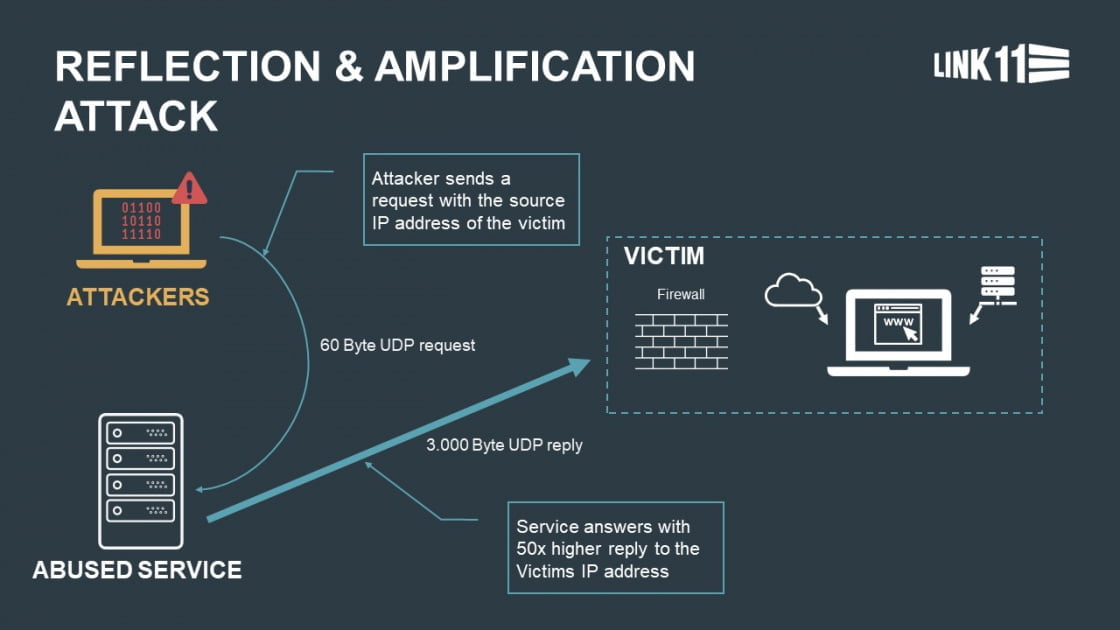
DDoS attackers abuse a multitude of Internet protocols to reinforce their attacks. Most techniques, also called vectors, belong to the reflection amplification category. DDoS reflection involves guiding the reply of a service to the IP address of the victim. The side effect is that the attack is virtually untraceable. This is called spoofing. Popular reflectors are DNS, NTP or CLDAP servers. The goal of DDoS amplification is to ensure that the reply packages sent to the spoofed sender are much bigger than the queries. This reinforcement potential is known as the amplification factor. In particular cases, a DNS server can reply to a 60-byte query with more than 3,000 bytes. This involves a amplification factor of 50. According to US Cert, the greatest known factor is 51,000 and can be achieved by memcached servers.
The first reflection amplification vectors occurred in 2013 and involved DNS and NTP. Since then, the spectrum of vectors has become far greater. Currently, there are over 20 techniques, including Memcached Reflection and CLDAP, and, since the second half of 2019, the WS Discovery and Apple Remote vectors. The chronology shows the occurrence of the most important vectors, along with their potential for danger.
Attackers constantly identify new vulnerabilities, inadequately protected Internet services, and open services that can be misused for overload attacks. It is only a matter of time before cybercriminals discover the next long-established protocol for DDoS attacks.