Content

Analyzing the Anonymous DDoS ‘Ping Attack’ Tool
Today, even beginners and technical laymen can easily launch a DoS attack, using one of the many free attack tools that have been made available. The Anonymous group has been making its DoS programs publicly available for years. One of these is the Anonymous Ping Attack tool, which is available on the clearnet and can be downloaded for free. It’s part of a set of tools that also includes tutorials, and enables any internet user to run denial-of-service attacks on any target of their choosing.
The program’s name refers to ping attacks, a specialized type of DoS attack. Generally, the purpose of a ping is to check the availability of other systems and to provide an indicator for the transfer time between two points on a network. Usually, they’re used to analyze connection issues and other incidents. Unfortunately, this type of traffic can be exploited for attacks. The Link11 Security Operation Center recently examined how the tool works, and how dangerous its attacks can be.
An easy-to-use denial-of-service tool
After downloading and unpacking the Anonymous ZIP archive, the installation of the program named Anonymous Ping Attack.exe doesn’t take long. A simple double-click on the icon will start the DoS attack tool. The user interface no longer has anything in common with earlier command line tools with hundreds of options. Instead, it comes with a modern look and an easy to use GUI.
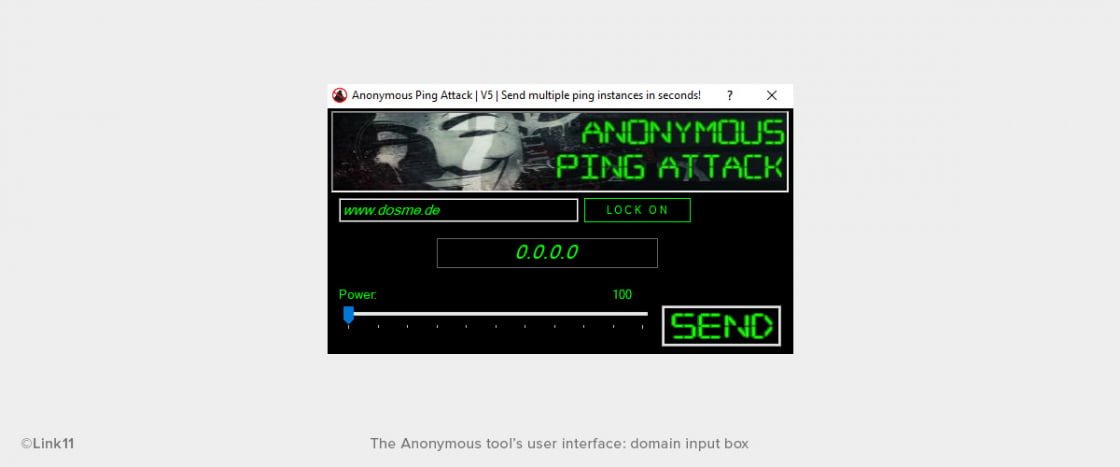
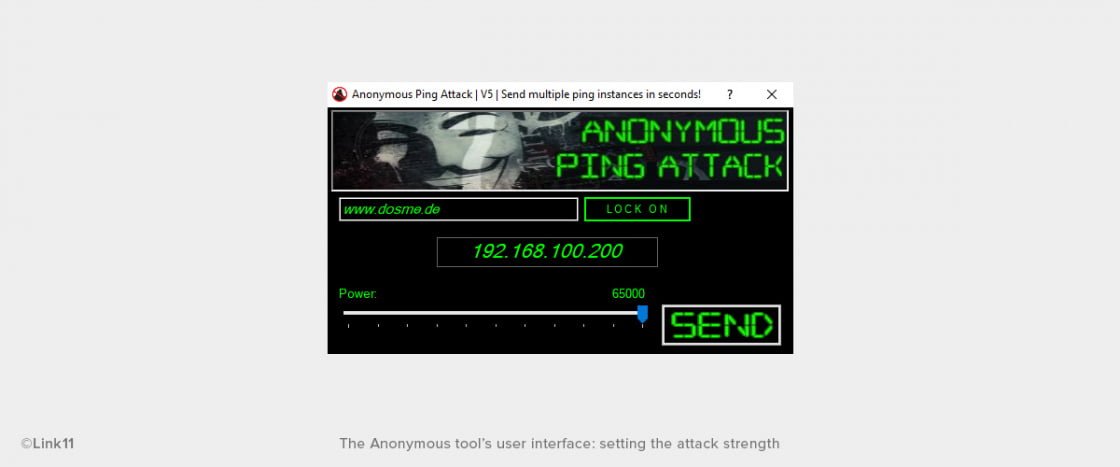
The work required from the user is reduced to a minimum. The only thing the user needs to do is entering the target’s FQDN (fully qualified domain name), e.g. the target website. (The LSOC operates the domain www.dosme.de for testing purposes.) With one click on the “LOCK ON” button, the target’s IP address is determined. No knowledge of how to resolve a DNS name is required. After that, a slider can be used to set the attack strength. The scale goes from 100 to 65,000 and determines the data size of a ping request in bytes.
The preparation of the attack is completed by clicking the “Send” button. Each send action launches an ICMP flood directed at the target selected. The program handles the rest.
Ping attacks analyzed
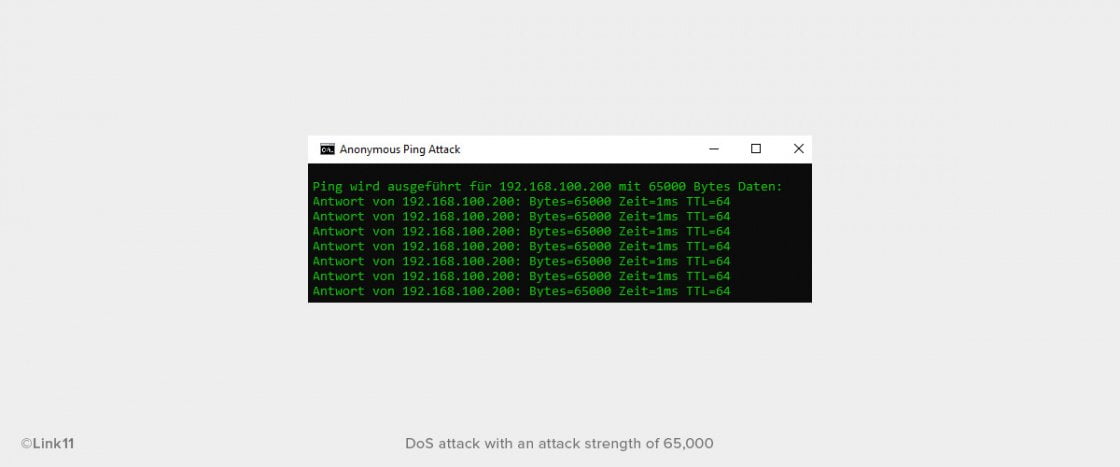
On each click on the send button, a CLI window will open.

In this case, a ping is sent that transfers 100 bytes of data. However, if the attack strength is increased to 65,000, pings with 65,000 bytes of data in each will be sent. This is how the CLI window changes in that case:
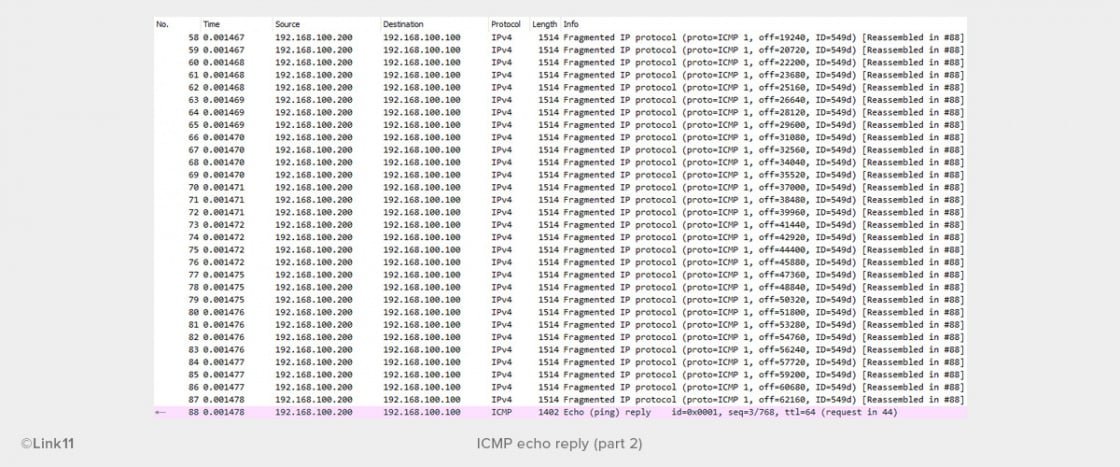
A single ping will not cause any problems for a server. The attacker sends 44 data packets per ping (ICMP echo request) in the direction of the target. The target will send the same number of data packets back to the attacker as an ICMP echo reply, as shown here:

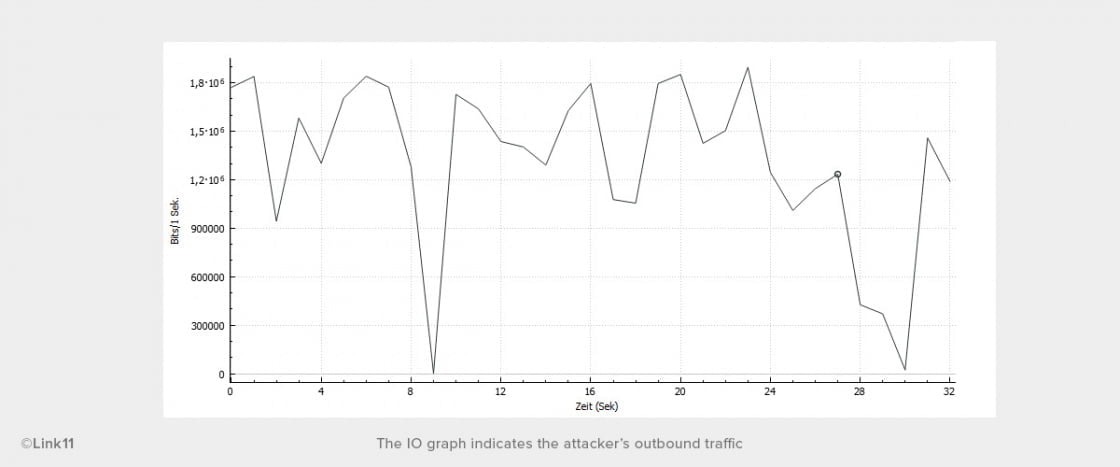
If the attacker launches multiple simultaneous attacks by clicking “SEND” several times, the target will soon be hit by thousands of packets per second. The IO graph indicates the attacker’s outbound traffic:
Strength in numbers
As a single attacker, the LSOC can generate approximately 2 Mbps of attack traffic. Viewed as an individual event, this is not much of an issue. However, as soon as a larger group of people jointly attacks a target, the attack volume can grow quickly to reach hundreds of megabits per second.
This illustrates how this simple, free tool could be used by almost any individual or group to launch a powerful, high-volume DoS attack against a target website or domain. To mitigate these high-volume targeted attacks, it is important to filter the attack traffic from regular traffic. A firewall (whether conventional or NGFW) will quickly be overwhelmed when there are too many requests at once. As such, organizations should consider using a cloud-based DDoS protection service which is capable of analyzing the traffic targeting the website, and can quickly identify and filter out malicious packets while ensuring safe delivery of legitimate traffic. This helps to ensure that normal business operations are not disrupted, even by long-lasting, high-volume attacks.