Content

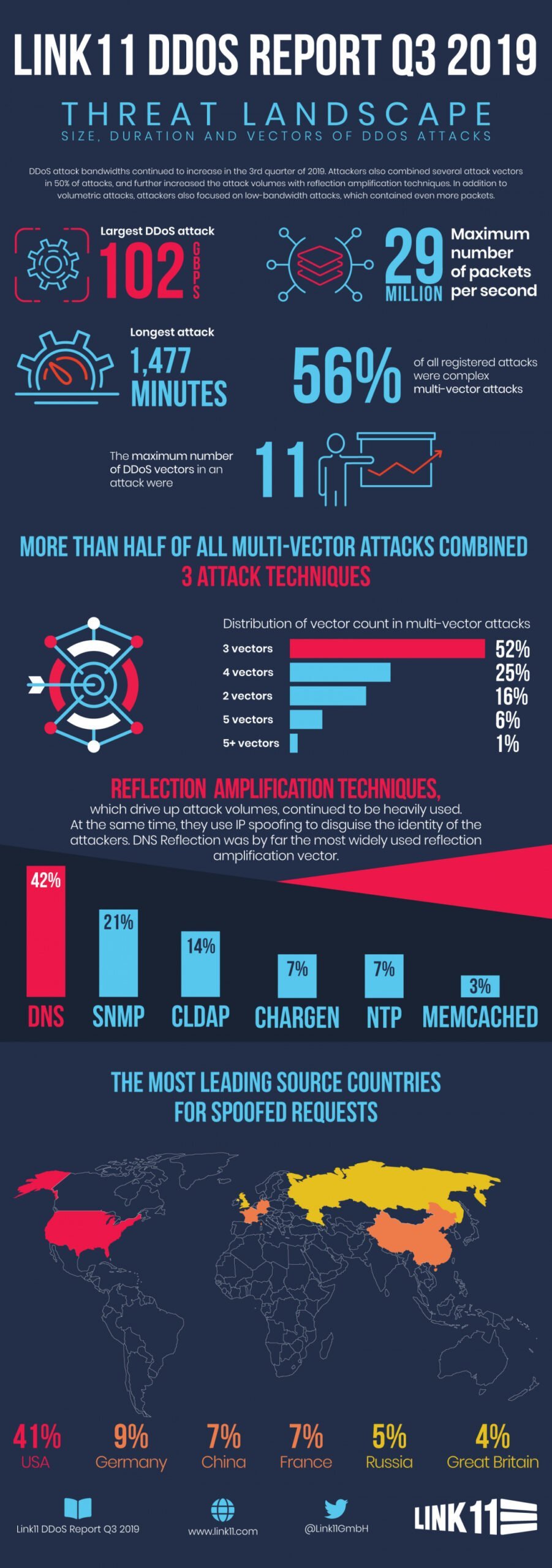
High bandwidth and complex DDoS attacks continued unchanged in the third quarter of 2019. Every second attack saw the attackers combining several attack vectors and driving up the attack volumes with reflection amplification techniques. Apart from volume attacks, the assailants concentrated on attacks with low bandwidths that made up for this by containing all the more packages.
Frankfurt, October 30, 2019 – The Link11 Security Operation Center (LSOC) has published new figures on the threat situation from DDoS attacks. Volume attacks remained the most important attack form in the third quarter of 2019. Such high bandwidth attacks are intended to block the attacked company’s external connection. In this quarter, the bandwidth peak was 102 Gbps.
Massive attack bandwidths due to reflection amplification techniques
In many cases, the attackers relied on reinforcement techniques to drive up the attack volumes. DNS reflection was by far the most frequently used reflection amplification vector (42%). This was followed by SNMP with 21% and CLDAP with 14%. New attack techniques, such as WS Discovery and Apple Remote, which were registered for the first time in the second quarter of 2019, were detected several times in attacks.
Moreover, every second attack (52%) was based on several attack techniques. Most frequently, the attackers combined three vectors. The maximum number of vectors up to now, registered by LSOC in the third quarter, was 11.
Application level attacks block server resources
Furthermore, the latest figures from network monitoring indicate that attackers are deploying application and protocol attacks more and more frequently. Attacks at application level are aimed directly at application functions and APIs, but not at the Internet connection. Their aim is to cripple the processes and resources for layer 7. Low bandwidths and high package rates are characteristic for application attacks.
“Analyses show that there is no cause for an all-clear,” according to Rolf Gierhard, Vice President Marketing at Link11. “Attackers are increasingly combining multiple attack techniques or expanding their attack set with new protocols. Attacks are becoming more intelligent and disguising themselves as legitimate network traffic. This makes it difficult for many companies to detect them quickly and effectively avert them.”
The data is based on defended attacks on websites and servers that are protected by Link11. In addition to network analyses and the evaluation of DDoS attack data, the Link11 DDoS report also makes use of open source intelligence (OSINT) analyses. Alongside the figures, further information on DDoS attacks and blackmail can be obtained from the Link11 blog.