In January, our analysts observed an unusual attack pattern at a major European e-commerce provider. It was not a classic DDoS attack with massive traffic volumes. Instead, over several weeks, there was a subtle, recurring increase in load that noticeably slowed down the web shop on Mondays.
This case is exemplary of a new generation of attacks in which infected end devices with legitimate browsers are used to deliberately exhaust server resources. There was no sudden peak and no alarm in the backbone. Rather, it was a quiet, systematic slowing down of a productive platform.
A pattern that didn’t fit the business
On normal days, the number of unique IP addresses remained stable at under 2,000, but on several Mondays, this figure regularly doubled to between 4,000 and 6,000.
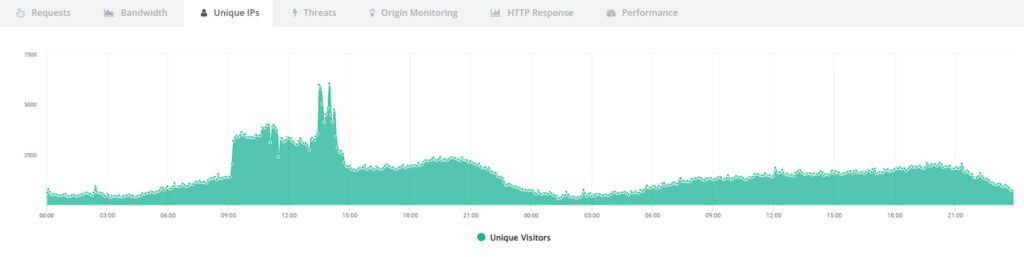
At first, this seemed like a harmless fluctuation in traffic. However, a review of business activities revealed a clear picture: there were no campaigns, no newsletters, no special offers, and no increased social media activity.
In short, there was no legitimate reason for this recurring increase.
What was particularly striking was the regularity. The effect occurred exclusively on Mondays, week after week, and disappeared completely on all other days. This temporal pattern alone was unusual enough to trigger a deeper analysis.
Low traffic, big impact
At first glance, the technical metrics seemed unremarkable. Neither the bandwidth nor the requests per second stood out.
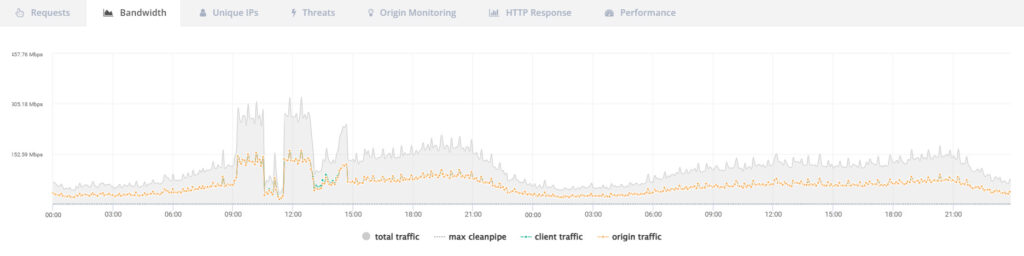
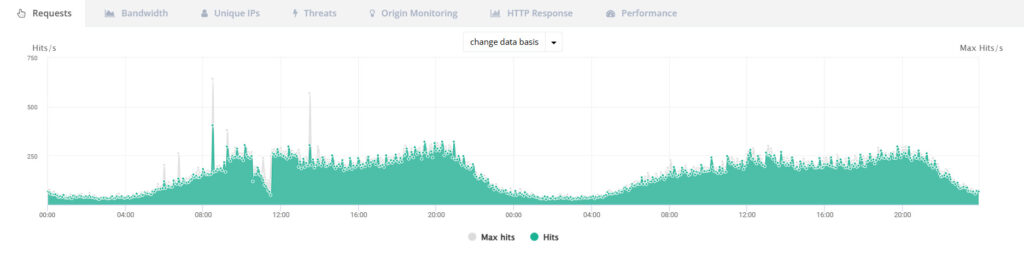
Only upon closer inspection did the actual problem become apparent.
The load was distributed across a large number of sources, each of which was only minimally active. There were several characteristic features:
- Only one to two requests per IP.
- Many connections remained open for an unusually long time.
- Hardly any simultaneous peaks, but rather a steady continuous load.
- Hardly any fluctuations in the classic volume metrics.
As such, this did not result in a classic attack, but rather a creeping consumption of resources. The CPU, memory, and connection handling of the origin servers were increasingly running at their limits.
The measurable result was response times of less than 200 milliseconds, which rose to several seconds on the Mondays affected. For a web shop, this meant slow pages, abandoned shopping carts, and declining conversion rates, without any clear trigger.
When protection systems see nothing
What was particularly critical was that the existing bot management system classified the traffic as almost entirely legitimate. There were no conspicuous user agents, unusual request sequences, or suspicious protocol errors. The origin of the requests also appeared harmless.
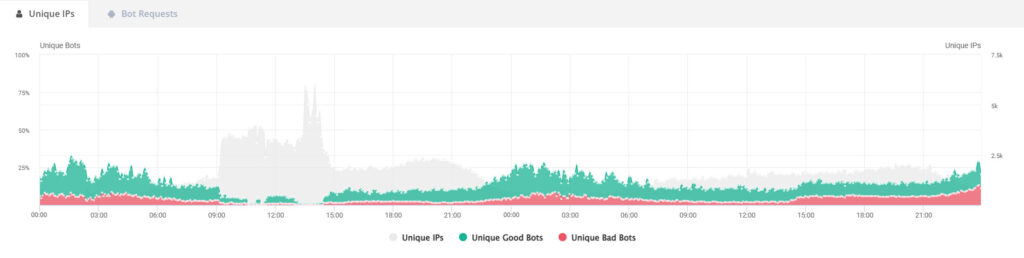
Most of the traffic came from Germany from typical end-customer networks of large consumer providers. Neither geo-blocking, ASN blocking, nor IP reputation filters provided any useful clues.
Everything pointed to the fact that these were not classic server bots, but real, compromised end devices with full-fledged browsers. Each individual device behaved almost inconspicuously. It was only the sheer volume that made the attack effective.
Low-and-slow with real clients
The pattern matched a classic low-and-slow attack. There were many sources, low activity per source, technically clean protocol behavior, and a clear focus on open connections rather than bandwidth.
Such attacks are particularly dangerous because they hide in the statistical noise of normal user activity. They do not trigger classic thresholds and almost completely bypass signature-based detection.
Added to this was the strange time restriction to a single day of the week. It was not possible to clearly determine why the attack took place exclusively on Mondays. Possible reasons include:
- Automated test runs of a botnet.
- Training phases prior to larger campaigns.
- Targeted stress tests of the infrastructure.
- Preparatory reconnaissance.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
A simple test with a big impact
After all classic analysis and filter mechanisms had been exhausted, only one option remained: the activation of a global CAPTCHA defense.
The customer was initially hesitant. Their concern about a negative user experience was justified. Nevertheless, the measure was activated in a controlled test.
The effect was evident within seconds:
- A significant reduction in the load on the origin servers.
- Normalization of response times.
- Over 99 percent of suspicious requests were blocked.
The web shop was running stably again, with no significant impact on real users. It was now clear that, despite coming from legitimate clients, these were automated processes.
What this attack teaches us
This incident highlights several key developments in modern attacks:
- It is not volume that matters, but precision.
- Real devices are increasingly becoming attack platforms.
- Classic bot management is not sufficient for clean traffic.
- Human-machine checks remain an effective tool.
Low-and-slow attacks show how easily modern infrastructures can be slowed down below classic alarm thresholds without setting off any triggers.
Modern defense instead of reactive emergency solutions
In the security architecture used, CAPTCHA was the last available lever. Such attacks can be defended against much more elegantly on modern web application protection platforms.
Instead of explicit CAPTCHAs, behavior-based methods are used, including JavaScript challenges in the background, headless browser detection, browser fingerprinting, and the correlation of sessions over longer periods of time. These mechanisms remain invisible to real users, but compromised clients fail reliably.
New reality in the bot age
Anyone who only pays attention to volume, signatures, and classic bots today overlooks precisely this type of attack. Modern defense requires a combination of behavioral analysis, human verification, and fine-grained traffic control.
For IT decision-makers, this means one thing above all else: anomalies in the number of unique IPs are not a marginal phenomenon, but often the earliest warning sign of a silent but effective attack.
If your web applications are also suffering from unexplained load peaks, increasing latencies, or suspicious access patterns, we would be happy to assist you in analyzing and securing your infrastructure.
Contact us—before a silent anomaly turns into a real failure!

 Lisa Fröhlich
Lisa Fröhlich