Content

In late February 2018, the Link11 Security Operation Center discovered massive UDP attacks using UDP source port 11211. This type of attack was previously unknown. These current attacks thus represent the appearance of a new amplification vector, which the Link11 DDoS security experts call “Memcached Reflection” after initial analysis.
The attacks began on several consecutive days; the duration of the attacks is currently up to ten minutes. The attacks are particularly dangerous due to their high bandwidths, which exceeded 100 Gbps during every attack. Furthermore, the peaks of these hyper attacks went well beyond 400 Gbps.
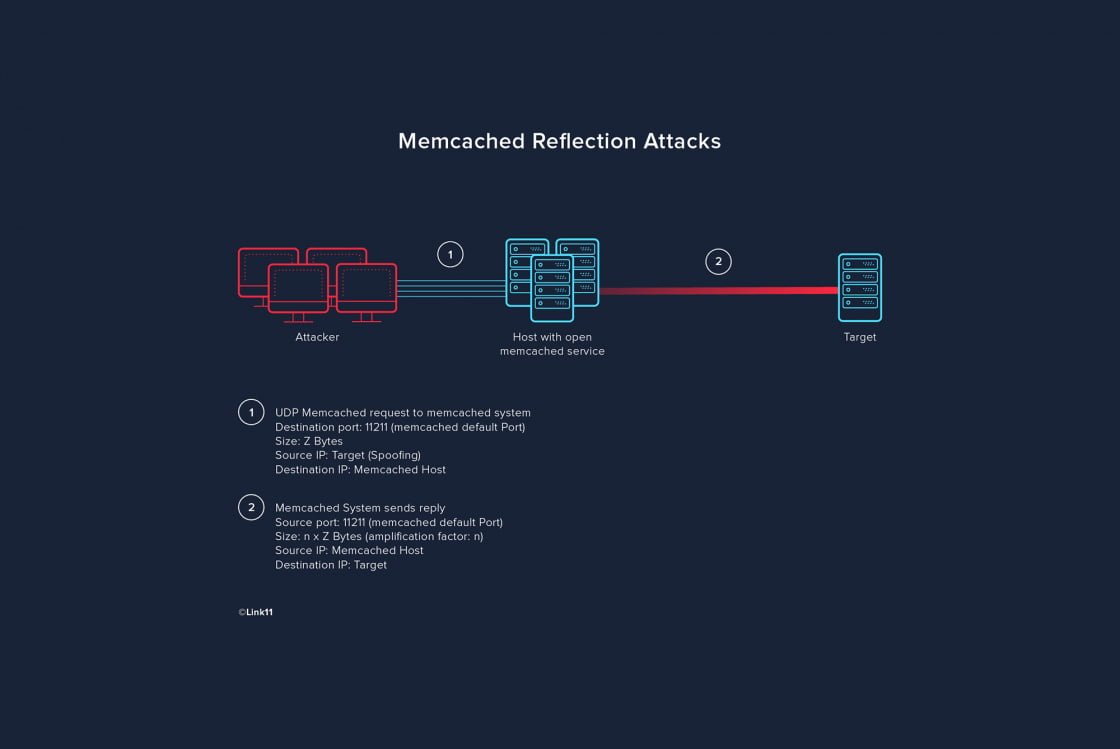
Memcached reflection attacks fall into the class of reflection amplification attacks and are similar to DNS reflection. Memcached is a free, high-performance object caching system under open source license. It is used to accelerate dynamic web applications, as objects and other data can be temporarily stored in the server’s main memory. The attackers exploit the free caching system’s poorly secured installations: it can be reached unsecured via UDP port 11211 for reading and writing data, as well as querying statistics.
Memcached reflection attacks use freely available servers on the internet which have installed Memcached. These servers are used as “amplifiers.” The attack itself is relatively simple: first, potential amplifiers are searched for using UDP internet scans on port 11211. The attacker then makes (tens of) thousands of requests to the corresponding servers using the IP address of the attack target, so that the responses of the Memcached instances are not sent to the attacker but to the target of the attack. (Tens of) thousands of answers are sent from the Memcached hosts to the target of the attack.
Attack characteristics
Attack vector: Memcached Reflection
Peak Bandwidth: 460 Gigabits per second (previously)
Source Port: 11211
Memcached Reflection Attack
2018-02-xx 02:34:56.628098 IP S1.S1.S1.S1.11211 > Z.Z.Z.Z.47834: UDP, length 1150
2018-02-xx 02:34:56.628100 IP S2.S2.S2.S2.11211 > Z.Z.Z.Z.57156: UDP, length 1150
2018-02-xx 02:34:56.628101 IP S1.S1.S1.S1.11211 > Z.Z.Z.Z.35003: UDP, length 1150
2018-02-xx 02:34:56.628102 IP S1.S1.S1.S1.11211 > Z.Z.Z.Z.51276: UDP, length 1150
2018-02-xx 02:34:56.628104 IP S2.S2.S2.S2.11211 > Z.Z.Z.Z.24129: UDP, length 1150
2018-02-xx 02:34:56.628107 IP S3.S3.S3.S3.11211 > Z.Z.Z.Z.61202: UDP, length 1150
The actual requests to the memcached host are quite small, while the answers are many times larger. Analysis of the attacks showed that the amplification factor can climb into the thousands. Even an attacker with a relatively small bandwidth connection can launch attacks of greater than 100 Gbps with minimum resource input.
| Country | Count |
| US | 452 |
| FRA | 205 |
| NL | 117 |
| CAN | 108 |
| JPN | 75 |
| UK | 55 |
| RUS | 36 |
| VNM | 31 |
| IND | 31 |
| BRA | 20 |
| TUR | 16 |
| THA | 15 |
| GER | 14 |
| POL | 13 |
Conclusion
Memcached reflection attacks are a serious threat as the amplification factor is always extremely high. It is also alarming that Memcached allows access to the data stored in the cache without any form of authentication. With free access to port 11211 via UDP and TCP, third parties can easily access data in the corresponding caches and even modify them. Link11 recommends restricting external access to Memcached servers as much as possible.