Leading companies worldwide already trust in our solutions – be one of them.
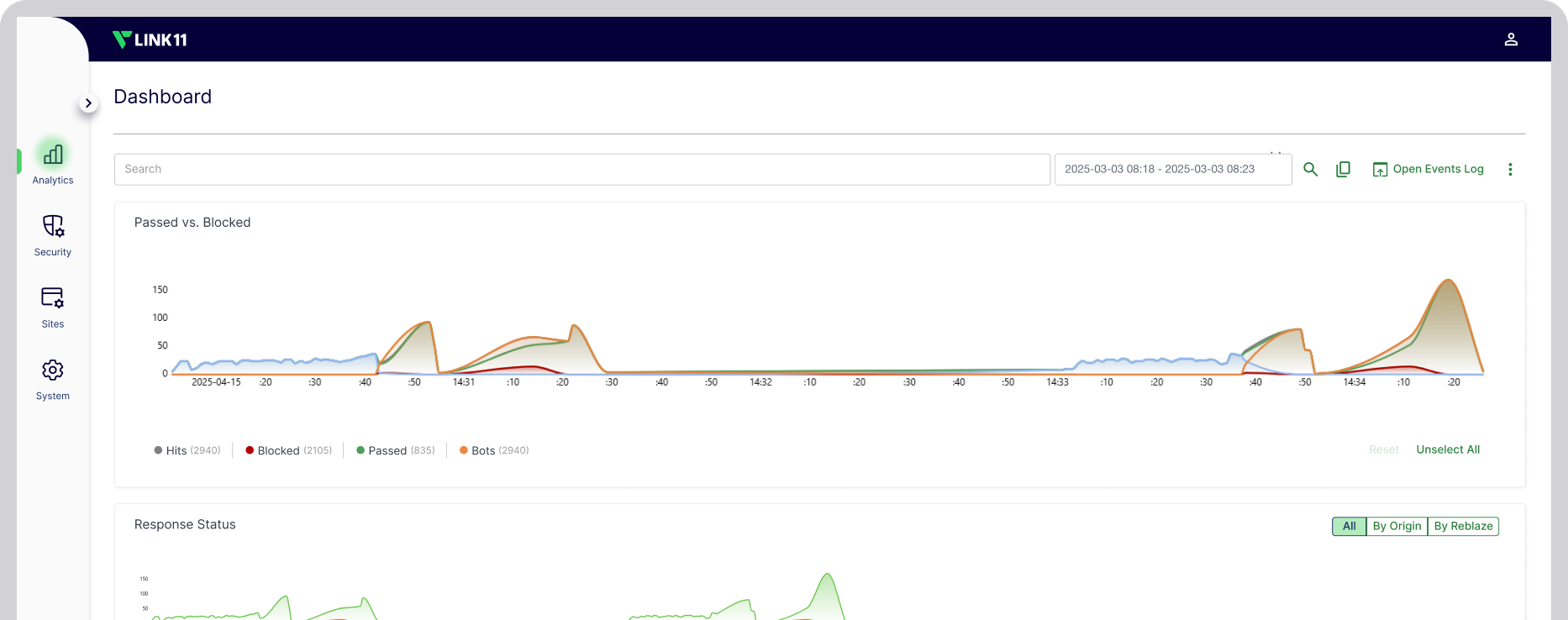
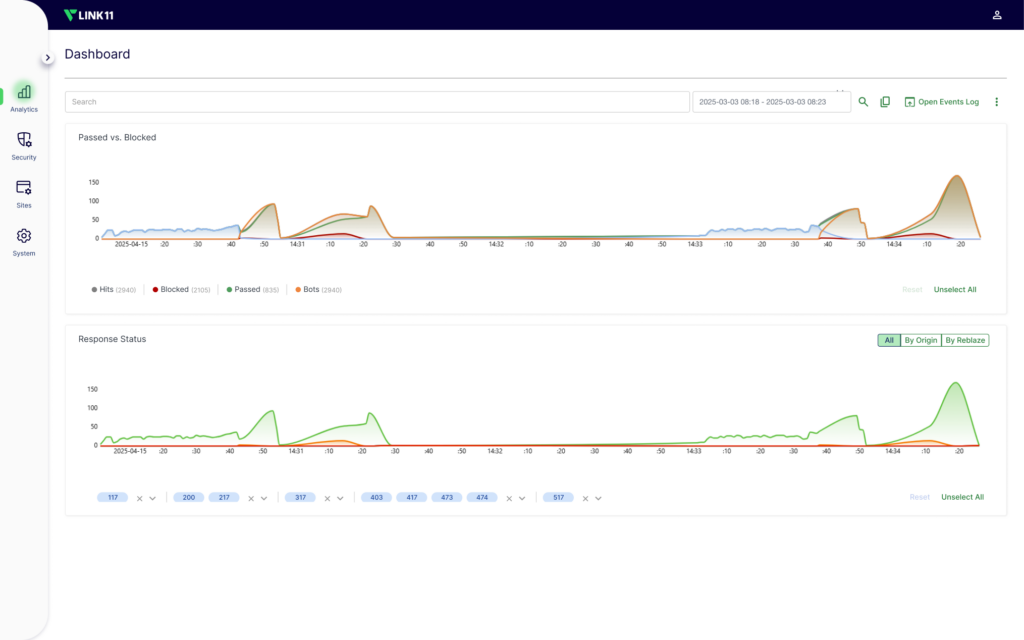
The Link11 Cloud WAAP platform delivers comprehensive, multi-layered protection for essential web assets. Web applications, and APIs are protected around the clock – maximizing service availability, optimizing performance and providing peace of mind.
Our proven combination of Web Application Firewall, Web DDoS Protection, Bot Management, and API Security already safeguards millions of web applications and APIs for medium-sized businesses and enterprises worldwide.