Content

End of April 2025: While the political debate in Germany is coming to a head over the planned delivery of Taurus cruise missiles to Ukraine, a digital offensive has begun in its shadow. Pro-Russian hacker groups – led by NoName057(16) – are intensifying their attacks on German companies, institutions, and cities.
Within a few days, websites of state banks, industrial companies, and city administrations are paralyzed by targeted DDoS attacks. NoName claimed responsibility for the attacks via Telegram, marking a new level in geopolitically motivated cyber warfare against German targets.
While portals such as berlin.de, stuttgart.de, and nuernberg.de were unavailable for hours or even days, simultaneous attack attempts were recorded on company websites such as Volkswagen, Lidl, and Commerzbank.
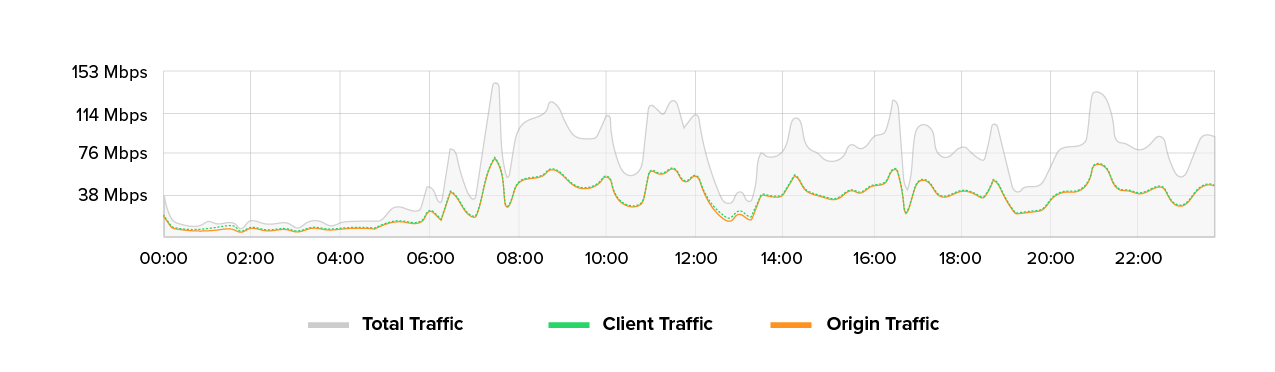
We observed a Layer 7 DDoS attack on the Link11 network amidst this flurry of attacks that stood out not for its volume, but for its sophistication. There was no brute force data stream and no millions of packets per second, but rather a precise attack.
What is a Layer 7 DDoS attack?
A Layer 7 DDoS attack targets the top layer of network communication, the application layer. Typical forms of attack include sending massive numbers of HTTP requests to web servers or APIs in order to exhaust backend resources.
Unlike volumetric attacks, the strength of these attacks lies not in their bandwidth, but rather in the large number of intelligent, legitimate HTTP requests. These are difficult to distinguish from regular traffic.
Camouflaging with structure
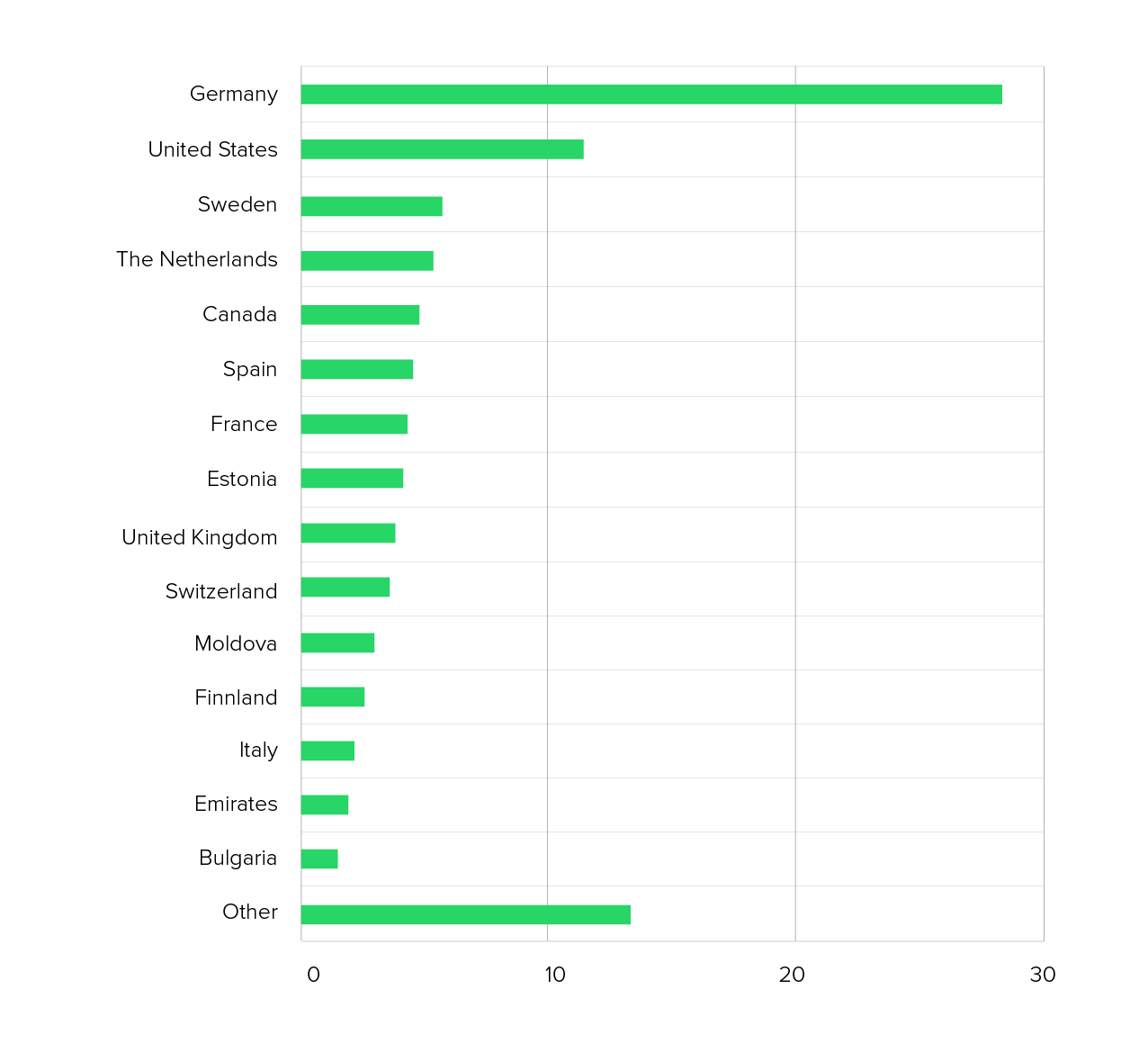
At first glance, the attack appeared unremarkable: no unusual volume, no exotic countries of origin. What made it noteworthy, however, was the targeted use of well-known hosting providers whose infrastructure is also used by many VPN services.
The most important features:
- IP ranges from Datacamp Limited and M247 Ltd.
- These providers are frequent hubs for VPNs such as NordVPN and ProtonVPN, as well as for CDNs such as CDN77.
- The HTTP requests were evenly distributed, structured, and designed for long-term use rather than overload.
This approach made immediate detection difficult, especially since the attack traffic was virtually indistinguishable from legitimate traffic.
The perfect mask
A key component of the attack was the consistent use of obfuscating infrastructure. Instead of relying on open bots or conspicuous proxy servers, the attackers routed their requests through networks that are normally used for performance optimization and data protection.
Tactics used for concealment:
- VPN and CDN tunneling: The attacks were routed through services that specifically enable Geo-IP obfuscation.
- Geotricks via edge nodes: Despite globally distributed source systems, many requests appeared to originate from Germany because they were routed through nearby CDN nodes.
This technical game of hide-and-seek made it nearly impossible to trace the actual sources of the attacks.
No storm, just pinpricks
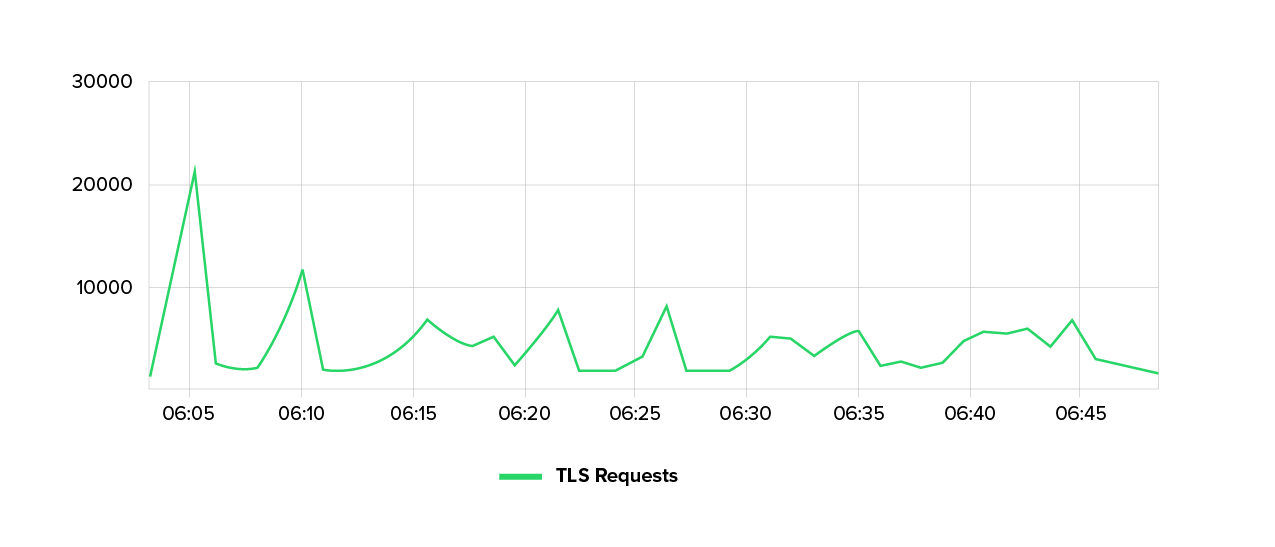
The Layer 7 DDoS attack we investigated did not rely on massive amounts of data, but on targeted, tactically placed disruptions. At its peak, we recorded around 20,000 requests per minute. While this is not enough to immediately paralyze large systems, it is enough to have an impact on sensitive areas.
When machines fail because they want to appear human
A particularly interesting aspect was the way in which the protection solution detected and partially blocked the attack. The attackers had apparently tried to simulate human behavior, but they did not succeed completely.
The most common reasons for blocking were:
- Unusual HTTP header combinations (e.g., missing referrers, inconsistent user agents).
- Suspicious visitor profiles that did not “stabilize” via cookies or JavaScript challenges.
- Failed interactions with CAPTCHA or JS fallbacks, indicating simple bots.
Although the attack was technically sophisticated, it failed due to the lack of complexity of human browsing patterns – a good sign for modern protection solutions.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
DDoS for the small budget
The economic efficiency of this attack was also remarkable. The technical effort was low, but the impact was nevertheless measurable. Especially when compared to the parallel large-scale attacks on municipal portals, a possible pattern emerges here: the targeted use of limited resources to disrupt digital processes.
Economic aspects at a glance:
- Low entry costs: VPN access usually costs only a few dollars, and in some cases is available for free via trial accounts.
- Microjobs for routine tasks: The mass creation of accounts or the rental of test servers can be outsourced for pennies.
- “Gold farming” logic: As in online games, monotonous tasks could be carried out in low-wage countries to build up attack infrastructure.
This development makes it clear that DDoS is no longer just a question of financial resources, but also of organization and intelligence in its construction.
Conclusion
The attack was designed less for brute force than for precision and concealment. Whether it was carried out by an inexperienced actor with limited resources or a larger group in the testing phase remains unclear.
One thing is certain, however: the ability to conceal the source of an attack makes it much more difficult to trace. This kind of DDoS attack is therefore a dangerous weapon in the arsenal of modern attackers.
Against the backdrop of the recent wave of attacks on municipal websites, it is clear that such Layer 7 techniques are not just isolated incidents, but are apparently becoming part of a strategic escalation against government and public IT infrastructures.
Covert, precise, difficult to detect – Layer 7 DDoS attacks require automated, intelligent protection strategies. Talk to our experts and we will advise you personally.