Content

A recently documented DDoS attack on the Link11 network has revealed a new level of complexity in today’s attacks. In particular, it highlighted the increasing sophistication of cyberattacks and the need to continually adapt defenses.
The attack: a complex interplay of DDoS methods
The attack was a complex interplay of DDoS methods and what makes this attack so remarkable is the rare combination of Layer 3/4 and Layer 7 attacks. Typically, attackers focus on one of these layers to achieve their goals. In this case, however, a hybrid approach was used with the intention of overloading both the network infrastructure and the application layer at the same time.
Layer 3/4 attacks target the network layer, attempting to exhaust available bandwidth and server capacity with massive amounts of data and manipulated packet streams. Layer 7 attacks, on the other hand, target the application layer, systematically attacking web applications and APIs to overload resources such as CPU and memory.
Attackers use an impressive variety of techniques:
- Layer 3/4 attacks: These target the network layer to overload the infrastructure.
- Layer 7 attacks: These focused on web servers and APIs to exhaust their resources with an immense number of HTTP requests. Peaks of up to 630 requests per second were recorded, well above the normal level of the targeted site.
- High number of requests: A total of 120 million requests were generated, triggering over one million Web Application Firewall (WAF) logs.
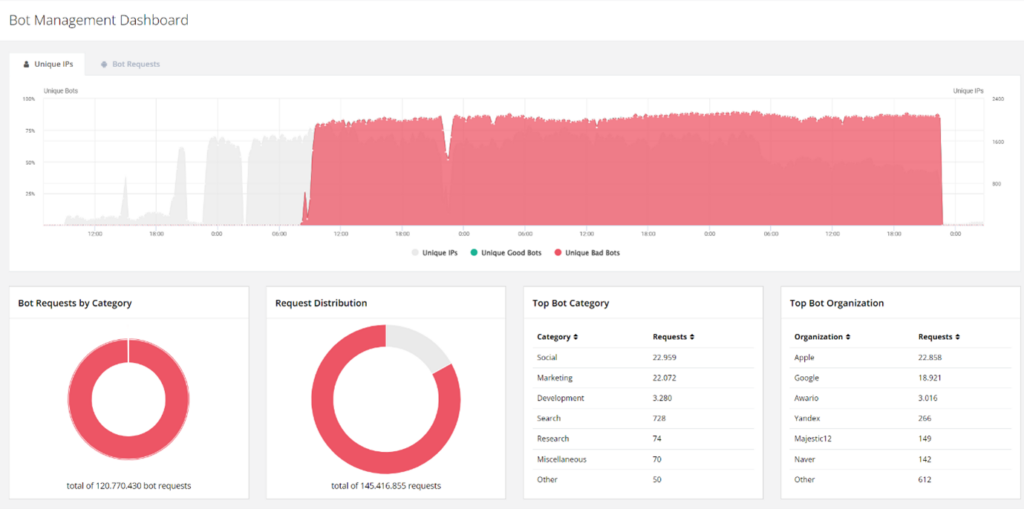
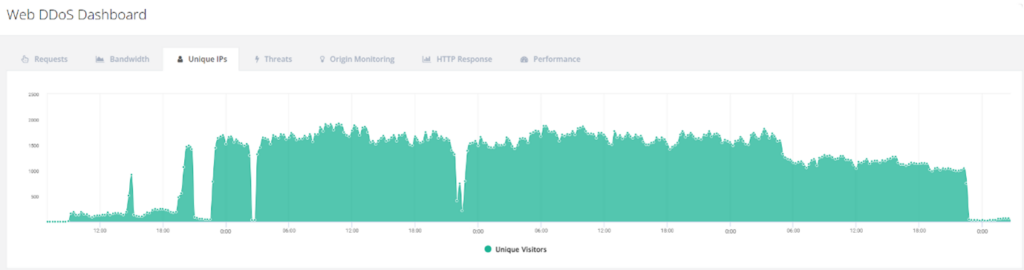
- Concurrent IP addresses: Up to 2,000 unique IPs were used simultaneously, a strong indication of a global botnet.
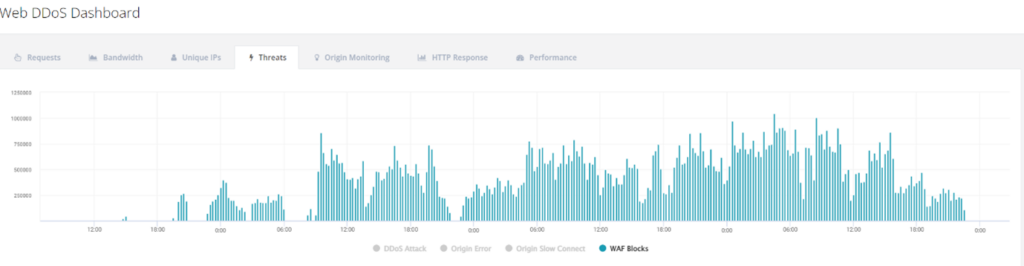
- Millions of WAF blocks in just 30 minutes – a volume far beyond normal levels.
- Adaptive attack strategies that respond to activated defenses.
- Constant attempts to circumvent WAF rules by testing different payloads.
Another indication of the attackers’ professionalism was the use of outdated user agents, such as Windows XP and browser versions older than five years. This suggests the use of automated botnets made up of compromised systems around the world.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Attackers with high resources
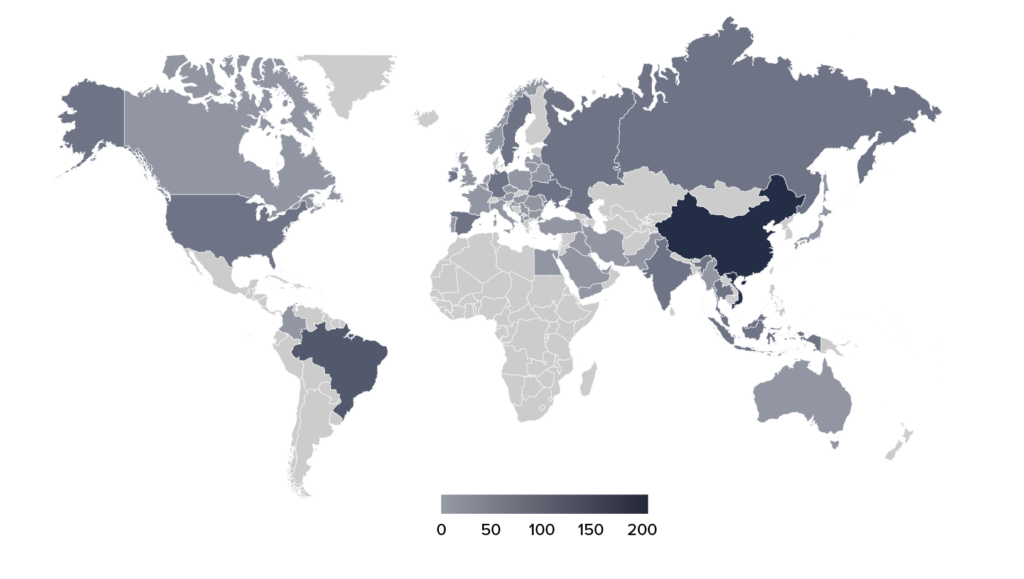
The origin of the attacks was as remarkable as their complexity. They came from networks such as Viettel Group, China Telekom, TOT and Yemen.net – companies not normally associated with DDoS attacks. This suggests that the attackers had significant resources and a well-organized infrastructure.
Geographic distribution of the attack
The ability to block a large number of IP addresses simultaneously and generate 8 million requests in just four hours costs thousands of dollars. This alone underscores the financial and technical resources of the attackers.
Possible motives
An attack of this magnitude comes at a significant cost. The reason is still speculative, but it is likely to be politically motivated hacktivism, an attack on behalf of political actors, or the use of DDoS-as-a-service.
The complexity and sophistication of the attack rules out a random hacker or script kiddies. It is more likely that this is a well-organized group with significant resources.
“Test Run” to Optimize Future Attacks?
The attackers systematically tested all available attack methods to determine the effectiveness of their techniques against the defenses of the target systems. Not only did the attackers use different methods in parallel, but they also appeared to be experimenting with different attack patterns:
- Testing the defenses: The attacks were periodically interrupted and then resumed with new techniques.
- Gradual scaling: Fewer IPs were used in the beginning, while the number of addresses used increased dramatically in later phases.
- On-off scenario: Brief pauses in the attacks suggest that the attackers deliberately waited for defenses to respond.
The role of bot management and web application firewalls (WAF)
Defending against this complex attack required the use of advanced protection mechanisms such as bot management and web application firewalls (WAF). Enabling a continuous protection mode (“attack mode”) was critical to ensure that the protection mechanism was not disabled by the attackers’ “on-off” tactics. The WAF recorded more than 2 million blocks in just 30 minutes, illustrating the intensity of the attack.
WAAP Responds to New Threats
Traditional security strategies often fall short in these scenarios. WAAP offers a more comprehensive solution that combines several protection mechanisms:
- Web Application Firewall (WAF): Automatically detects and blocks attacks such as SQL injection, cross-site scripting and other exploits.
- DDoS Mitigation: Protection against volumetric, protocol and application attacks through intelligent traffic filtering and rate limiting.
- Bot management: Identify and block malicious bots through behavioral, fingerprint, and user agent analysis.
- API protection: Validate API requests, prevent unauthorized access, and protect against API-specific threats such as credential stuffing.
Conclusion
A holistic security strategy is essential because attacks on web applications and APIs are becoming more sophisticated and using a greater combination of techniques. Enterprises need to continuously adapt their security strategy and rely more on WAAP solutions. Modern WAAP approaches not only provide protection against known threats, but can also use AI-based anomaly detection to identify and defend against new types of attack patterns.
Today’s cyberattacks are more sophisticated than ever – and traditional defenses are often inadequate. Our WAAP service combines intelligent web application firewalls (WAF), API protection, bot management, and DDoS protection into one powerful solution. Contact us to schedule a meeting with our experts!