Content

A recent Web DDoS attack registered in the Link11 network clearly shows how high the load on an attacked website can be. The attack was an application layer attack with a high number of packets per second. The cyberattack not only reached a packet rate of 45 million packets per second, but also had an unusual combination of high packet rate and greatly increased packet volume (500 Gb/s).
The attack strategy had two objectives: first, a) to saturate the bandwidth, and b) to establish many connections to exhaust the CPU. This two-prong strategy was unique in this respect, leveraging volume and high frequency of packets per second. Usually, the focus of an attack is on one or the other, not both. To be able to generate such volume and rate, where either one by itself would saturate the capacity of most enterprise and hosting networks, is truly impressive.
Special Attack Features
- Multiple attack techniques: The attackers used both bandwidth saturation and server resource overload by opening a large number of concurrent connections.
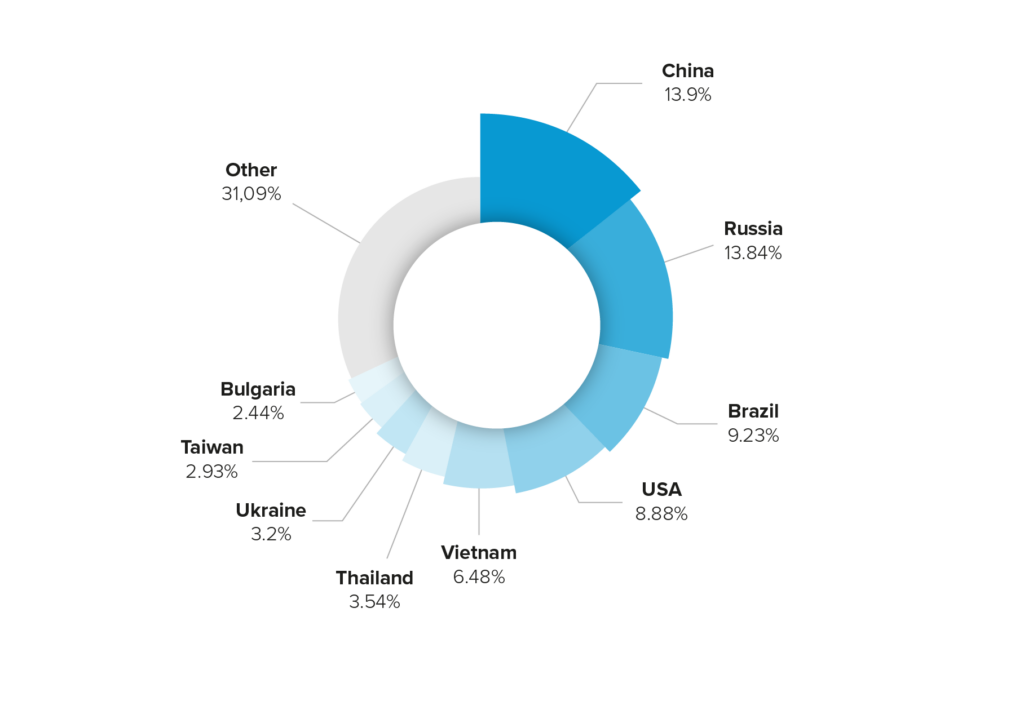
- Global origin: The attack originated from numerous countries, including China, Russia, and Vietnam, making it difficult to identify the attackers.
- Unusual packet size: Unlike typical DDoS attacks that send small packets in large numbers, the packets were larger than usual, averaging 1,400 bytes.
Attack Vectors and Techniques:
- TCP protocol: The attackers used the Transmission Control Protocol (TCP), a connection-based protocol that ensures that data arrives in its entirety and in the correct order. The attackers specifically targeted TCP port 443, the default port for HTTPS traffic, to overload the Web server. By sending a large number of connection requests, they attempted to exhaust the server’s capacity and eventually disconnect it from the Internet. Compared to a simple UDP flood, this type of attack is technically more demanding and requires more computing power.
- Diverse botnets: The attack was controlled by more than 30,000 compromised devices that functioned as a very widespread global botnet. It is believed that this large number of compromised servers and systems generated a high attack rate per second with a large amount of data.
- Packet fragmentation: The attackers fragmented large packets to evade firewall inspection and make detection more difficult.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Lessons from the attack
The ability to respond to an attack remains a challenge regardless of the size of the network. Organizations should have a contingency plan in place to quickly engage their Internet Service Provider (ISP), hosting provider, or cloud security provider to respond to an attack. It is important to implement tools and monitors to identify compromised targets on the network. This way, at a minimum, blackhole measures can be implemented to avoid collateral damage.
However, if you are operating systems that need 100% uptime, an appropriate defense strategy should be implemented. A complete mapping of the services running on the corporate network and the use of filters and ACLs (Access Control Lists) can help block unwanted traffic.
AI-based systems can detect suspicious traffic early and block it before it can cause damage. They also allow security measures to be continuously adapted to new threats.
Fast detection mechanisms and automated countermeasures are therefore essential to thwart such massive attacks. The high packet rate of the described attack highlights the importance of real-time systems.
Get comprehensive security and scalability. Our cloud security solutions provide the protection you need, and we have the capacity and processing power to handle DDoS attacks. Contact us anytime to set up a personal appointment!