Content

Despite a massive and sustained DDoS attack, Link11 was able to protect the client’s critical IT infrastructure. The attack was notable not only for its public target, but also for the methods used by the attackers. Below we take a closer look at the technical aspects of this attack.
Multi-stage attack tactics
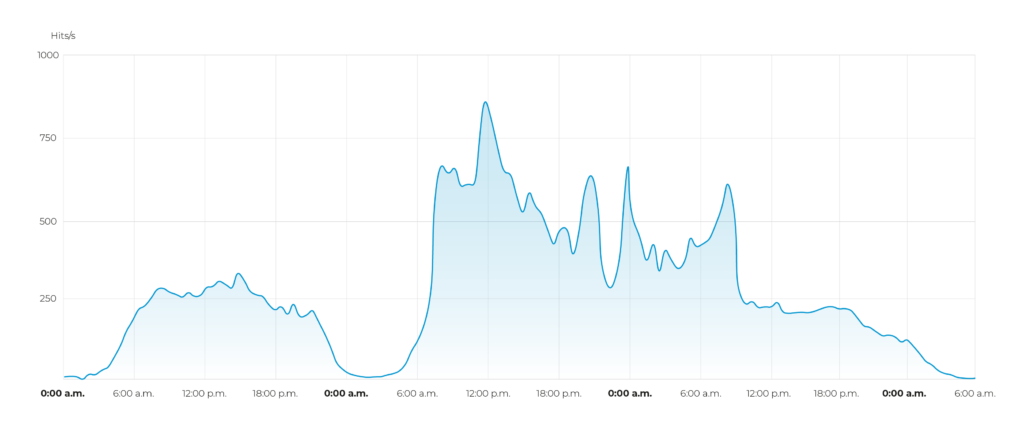
The attack tactics were multi-stage, starting with smaller, barely noticeable attacks that were cleverly integrated into normal traffic. These preparatory attacks were likely used to probe the system and identify potential vulnerabilities. This was followed by a massive attack that lasted almost exactly 24 hours.
Attacker obfuscation techniques
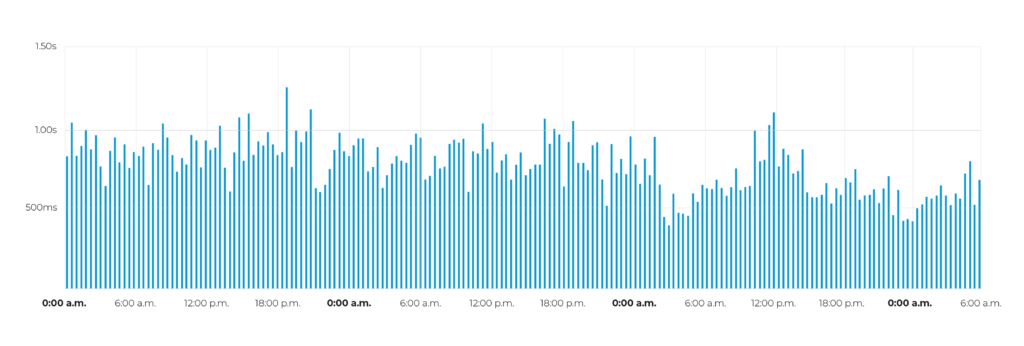
The attackers used a sophisticated technique to disguise their attack. They mimicked normal traffic so closely that the malicious activity was initially difficult to distinguish from legitimate traffic. A detailed analysis of the data was required to detect the manipulation of the traffic.
Attack Dynamics and Captcha Analysis
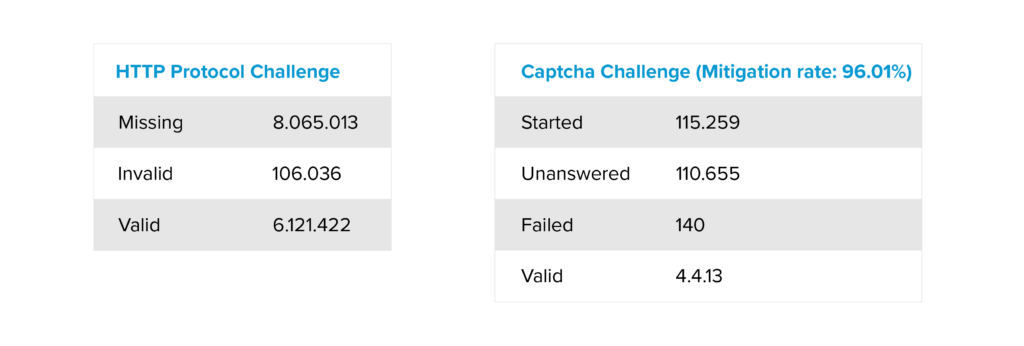
The attack had an unprecedented dynamic. The intensity of the attack reached a level within a very short period of time, indicating a precise and well-orchestrated action. A detailed analysis of the HTTP protocol shows that the activity is malicious. Traffic analysis revealed that a large proportion of requests were valid, but a strikingly high proportion were erroneous. The imbalance in the ratio of correct to incorrect requests clearly indicates that the protocol is being manipulated by malicious actors.
The analysis of the CAPTCHA results was particularly revealing. While a high CAPTCHA success rate would normally be expected for legitimate traffic, in the case of this attack, the success rate was only four percent. This drastic decrease suggests the use of bots. It should be noted, however, that the visual challenge alone is not the deciding factor.
Although some bots are able to solve the visual challenge, other parameters are also included in the evaluation, such as the speed of the solution or the pattern of mouse movements during the interaction. In particular, highly developed bots that execute JavaScript and actually solve the visual challenge could meet some of these requirements. However, the low success rate combined with the high number of failed HTTP requests clearly indicates a coordinated botnet attack.
The attack tactics in detail
The attack was very complex and persistent. The attackers used a multi-stage strategy to achieve their goals:
- In the reconnaissance phase, a large number of small attacks were first carried out to probe the system and identify potential vulnerabilities. Such attacks often go unnoticed because they can be hidden in legitimate traffic.
- The main attack occurred after the preparation phase and consisted of a massive DDoS attack that lasted almost 24 hours. The attackers used a large number of compromised devices to generate massive amounts of traffic. At the same time, there was no impact on the performance of the business.
- Traffic manipulation: To hide the attacks, the attackers mimicked legitimate traffic. However, analysis of the HTTP protocol revealed anomalies such as a high number of erroneous requests.
Indications of a Cybercrime-as-a-Service attack
The precise duration of the attack – almost exactly 24 hours – leads us to conclude that this was a cybercrime-as-a-service attack. DDoS attacks are often offered as a service on the darknet, with clearly defined time frames for carrying out the attacks. The cost depends on the duration, target, and complexity of the attack. The 24-hour period observed in this case corresponds exactly to one of the common offers on the darknet, which further supports the assumption of a commercially acquired attack.
A look at price lists on the darknet shows that a 24-hour DDoS attack against an unprotected website with a bandwidth of 10,000 to 50,000 requests per second can be purchased for around 35 US dollars. However, for a more sophisticated attack against a protected site using multiple elite proxies, the cost can quickly rise to $170 or more. Given the size and duration of the attack, it is likely that the attackers were willing to spend more to cause maximum disruption.
Origin of the attack
The network distribution was analyzed to distinguish between two common scenarios: the use of rented bots and the use of compromised devices. Rented bots typically show a concentration on a few large cloud providers. In contrast, this attack showed a broad distribution of attacks across many small networks. This pattern is characteristic of botnets made up of a large number of compromised home devices. The fact that the attacks originated from 110 different countries underscores the global reach of this botnet and makes it difficult to determine the exact origin of the attack.
Conclusion
The DDoS attack highlights the need to protect against such attacks. Organizations must continuously monitor and keep their IT infrastructure up to date. It is also important to be aware of the risks posed by botnets.
What can you do?
- Regular security checks
- Investment in a high-performance DDoS protection solution
- Raising employee awareness
- Partner with an experienced IT security provider