Web DDoS Protection
- Cloud-based DDoS protection for web applications
- Automation ensures 24/7 protection
- Zero time to mitigate for known, < 10 seconds for new vectors

No need to worry about complex attacks anymore: The system detects traffic anomalies and protects you from emerging threats in real time.
No work for you: manual operation is not required, and the system works fully automatically and without compromise.
Whitelisting, blacklisting, enhanced logs, traffic control, and more – helpful features help you make everyday life as easy as possible.
DDoS attacks continue to increase and still cause great damage today. In addition to the frequency, the complexity and duration of an attack cause major problems for the defense. Therefore, the deployed solution should intervene precisely and quickly to best protect you from threats and high costs due to downtime.
With Web DDoS Protection, you’ll be protected by a system that, thanks to artificial intelligence, effectively stops attacks on layers 3, 4, and 7. You’ll also benefit from numerous algorithms and heuristics that monitor and evaluate events at the application layer. With this combination, you can count on guaranteed mitigation of the attack within the shortest possible time.
Our system analyzes the typical traffic patterns of your web applications and identifies any anomalies that deviate from the “normal” or appear suspicious. This proactive approach ensures your protection not only against known threats but also against new and unknown ones.
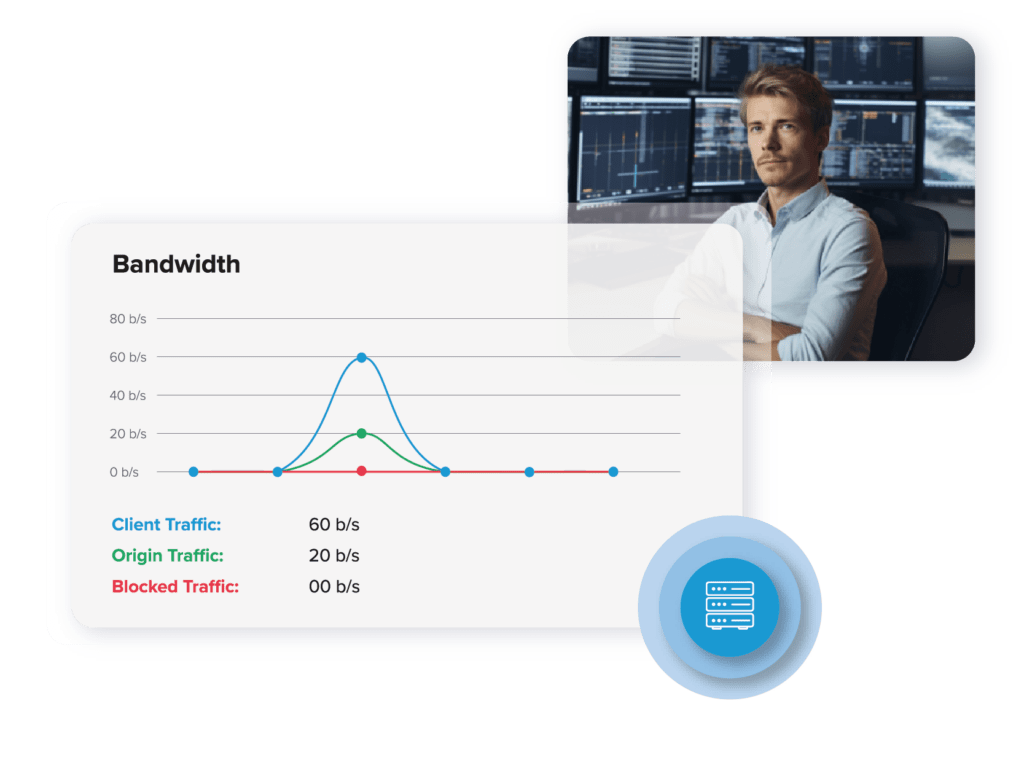
Our DDoS Protection makes your job as easy as possible. That’s why the security solution’s detection and mitigation tools work entirely without manual intervention. Attacks are detected and mitigated in real-time without you having to interact with the protection. This ensures that you and your applications are protected around the clock, at any time of day.
This automated security saves time and money and makes it even easier for you to focus on what matters most. Another advantage is that you don’t need to contact us in the event of an attack. Our system already knows and has taken all the necessary steps to mitigate the threat. Your everyday business can, therefore, continue as if nothing had happened.

Individual settings help you tailor the system ideally to your needs – our Web DDoS Protection offers just that. Provide the solution with your own certificate or use one from us, set up TCP port forwarding, or modify the geoblocking function. The choice is entirely yours.
The choices mean you don’t have to work with a rigid system that dictates what you can and can’t do. Take advantage of the flexibility and tailor your settings to the exact situation.

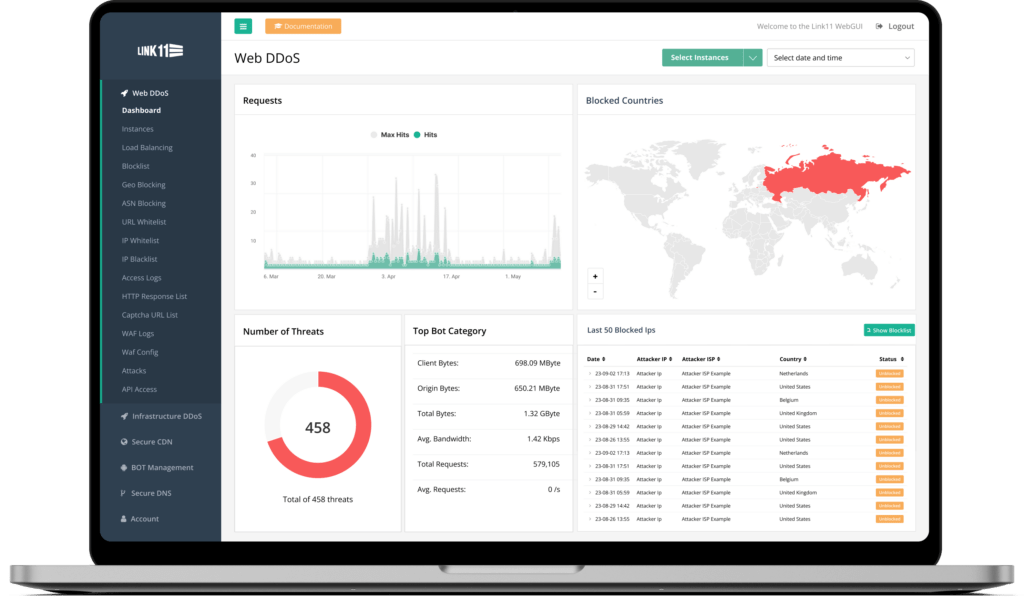
Everything at a glance: The dashboard shows key metrics, threat data, attacks averted, and data on bandwidth saved or traffic consumed. The flexibility of the data display is particularly noteworthy, as historical data can also be displayed via a data picker.
Reporting allows creating individual reports and scheduled reports, which can also be exported to PDF. In addition, there is function to send reports automatically at specified times.
User management gives administrators a detailed overview. User rights and security information can thus be conveniently checked and assigned. Details, such as the time of the last password change, and the activation of the two-factor authentication procedure can be found here.
Alarming: The notification frequency can be set in the contact settings. This allows customization so that users can be selected by products or areas of responsibility, for example. This way, only selected people can receive notifications and communication becomes more efficient.
Enhanced password management: Alphanumeric passwords and a configurable password length ensure that access is and remains secure. You can also use the WebGUI to set the maximum lifespan of passwords, prevent the reuse of older passwords and set a predefined limit for failed login attempts.
We protect more than two million assets of well-known customers worldwide. Our technology has more than proven itself during that process.
Our solutions are easy to integrate into any set-up. It is important for us that the effort for you is reduced to an absolute minimum.
For us, being there for you at any time is important. That’s why we offer 24/7 customer service in English and German to assist you in all topics.
Fully compliant according to the strict EU data privacy laws. Also, ISO 27001 is certified and officially qualified for the CRITIS sector by the Federal Office for Information Security (BSI).
Although Web DDoS Protection already provides a wide range of security, you can easily extend the protection standard with additional services.


“A failure of our systems would not only have consequences for us, but also for the many platform participants. At Link11, we are glad that they work reliably, quickly, openly and transparently. That reinforces trust in this service provider.”
Department head IT infrastructure
Pharma mall
Together, we will create a customized solution for protecting your web applications. Our security experts will happily support you and advise you without obligation on the benefits of our Link11 solutions for your company.